What Are Data Loss Prevention Tools?
Data Loss Prevention (DLP) tools are security solutions designed to detect, monitor, and protect sensitive data from unauthorized access, sharing, or leakage. These tools help organizations prevent intentional or accidental exposure of confidential information such as intellectual property, financial data, and personally identifiable information (PII).
DLP solutions can be deployed across endpoints, networks, cloud services, and storage to cover data in motion, at rest, and in use. Their main goal is to ensure sensitive data does not leave the controlled environment without proper authorization. They use a combination of content inspection, contextual analysis, and policy enforcement to identify and control sensitive data.
DLP tools integrate with enterprise systems to provide visibility into data flows and user activities that could lead to data loss. By implementing automated rules and policies, DLP tools can block risky actions, encrypt sensitive files, or alert administrators about policy violations.
In this article:
- Key Features of Enterprise Data Loss Prevention Tools
- Notable Data Loss Prevention Tools for Enterprises
Key Features of Enterprise Data Loss Prevention Tools
Data Discovery and Classification
Modern DLP solutions begin by identifying and classifying all types of sensitive data within an organization. Data discovery involves scanning endpoints, servers, databases, and cloud environments to locate confidential information, while classification tags data based on its sensitivity, such as public, internal, confidential, or regulated.
Advanced classification techniques also use content analysis, pattern matching, and contextual cues to accurately identify sensitive data, even if it is embedded or obscured. These features reduce false positives, ensuring that only genuinely sensitive information is subject to controls and allowing security teams to focus their efforts where they matter most.
Policy Enforcement
Policy enforcement within DLP tools enables organizations to define rules and actions regarding the handling of sensitive information. Policies might restrict the transmission of particular data types over email, block copying data to USB drives, or require encryption before sharing files externally.
The enforcement engine relies on patterns or classification labels to trigger predefined responses, ensuring that data handling aligns with both regulatory requirements and organizational policies. These controls can be tailored to roles, departments, or locations to support business operations without unnecessary disruption.
Learn more in our detailed guide to data loss prevention policy
Real‑Time Monitoring
Real‑time monitoring in enterprise DLP tools allows for immediate identification and intervention when sensitive data is accessed, transmitted, or modified. These tools continuously observe data movement within endpoints, networks, cloud environments, and external communications. Monitoring supports the detection of obvious policy violations and provides operational insight into data usage patterns.
Alerts generated through monitoring are typically enriched with contextual information, including user identity, activity timelines, and relevant data classification. This detail enables prompt investigation and response to incidents.
Incident Response and Reporting
Incident response features can quickly address and contain data loss events when they are detected. Automated response actions can include blocking user activities, isolating compromised devices, or revoking access rights, all of which aim to mitigate data exposure without waiting for manual intervention.
Comprehensive reporting features are essential for documenting incidents, tracking remediation activities, and meeting regulatory reporting obligations. DLP tools offer customizable dashboards and generate detailed incident logs that analyze root causes, data impacted, and mitigation steps taken. Reports can be tailored for technical teams, compliance officers, or executives.
Endpoint Data Loss Protection
Endpoint protection in DLP refers to the capability to monitor and control data on endpoints such as laptops, desktops, and mobile devices. As employees work remotely or access cloud services via a range of personal and corporate devices, endpoint DLP ensures sensitive information does not leave protected environments through local actions like screen captures, print jobs, or file transfers.
Endpoint protection measures often include file-level encryption, application control, and device policies that prevent data movement to unauthorized storage or devices. These tools persistently monitor user actions, offering granular visibility and enforcement even when traditional perimeter defenses are bypassed.
User Behavior Analytics
User Behavior Analytics (UBA) uses machine learning and statistical analysis to establish baseline user activity and detect anomalies that could indicate data loss risks. By continuously monitoring actions such as file access, modifications, or data transfers, UBA differentiates between normal behavior and potentially malicious or negligent activities.
This behavioral context is especially effective in detecting insider threats, compromised accounts, or privilege misuse that may bypass traditional signature-based controls. UBA-driven insights can trigger automated responses when behavioral deviations are detected, such as locking accounts or flagging users for additional investigation.
Compliance Support
Compliance support is important for enterprises subject to regulations such as GDPR, HIPAA, CCPA, or PCI DSS. DLP tools embed compliance-focused policies and templates, helping organizations automatically apply the right controls and generate required documentation. These tools can enforce rules around data residency, access, and handling, ensuring legal obligations are met without exhaustive manual processes.
Audit and reporting capabilities simplify regulatory inspections, supplying detailed logs and evidence of control efficacy. Automated classification and incident reporting also reduce the burden of preparing for audits, while transparent workflows support documentation and notification requirements.
Notable Data Loss Prevention Tools for Enterprises
Seraphic Security

Seraphic is a patented browser agent that seamlessly and instantly transforms any standard browser into a secure enterprise browser. Seraphic enables secure access to SaaS and private web applications to employees and third parties from managed and personal devices without the complexity and cost of VDI & VPN. Invisible to the end-user, Seraphic supports all browsers and SaaS desktop applications like Teams, Slack, Discord, and WhatsApp.
General features include:
- Real-Time Content Inspection: Monitors sensitive data such as PII, PCI, PHI, and intellectual property directly in the browser without relying on backhauling or traffic redirection.
- Policy-Based Enforcement: Apply granular policies—block, alert, or allow with justification—on data type, application, user identity, and action, all executed in real-time.
- User Action Control (Copy/Paste/Upload): Prevents or controls actions like copying data, uploading sensitive files, or pasting classified content into unauthorized browser fields or applications.
- Alerting and Logging: Logs all browser-based activity related to data access or movement, with customizable alerts for policy violations or risky behavior.
- Regulatory Compliance Support: Helps meet compliance standards like HIPAA, GDPR, CCPA, and PCI-DSS by enforcing policies where data is most frequently accessed—within the browser.
Enterprise features include:
- Browser-Level Visibility and Control: Provides deep inspection and control within any browser, allowing organizations to prevent unauthorized data interactions before they occur.
- Unmanaged and BYOD Device Protection: Enforces full DLP capabilities—even on unmanaged and BYO devices—without installing agents or requiring VPN, enabling secure contractor and partner access.
- Context-Aware Access Enforcement: Dynamically enforces policies based on user, location, device posture, application sensitivity, and data classification—all in real-time.
- Inline User Coaching: Prompts users with contextual policy notifications, warnings, or justification pop-ups to deter risky behavior and encourage compliance.
- Full Session Logging: Captures user interaction data—including DOM-level activity, copy/paste attempts, screenshot events, and more—for enhanced forensic auditing.
Cyberhaven
Cyberhaven is a DLP solution that uses a combination of content analysis and data lineage to track and protect sensitive information across all channels of exfiltration. Cyberhaven aims to reduce false positives and provide a more accurate understanding of what data is critical.
General features include:
- Content analysis and data lineage: Combines traditional content inspection with data lineage, allowing identification of sensitive data and its journey through the organization.
- Unified policy framework: Applies a single policy across all data exfiltration channels (email, cloud storage, USB drives, etc.).
- Cloud-based deployment: Delivered entirely from the cloud, eliminating the need for on-premises infrastructure.
- Visual policy editor: Allows easy creation and management of DLP policies using Boolean logic, with auto-completion for source and destination applications, URLs, devices, and user groups.
- OCR for image and PDF files: Extracts text from images and PDFs, enabling content-based policy enforcement on traditionally unscannable formats.
Enterprise features include:
- Incident response and data lineage: Tracks the lifecycle of data from creation through any exfiltration attempts.
- User education for risk reduction: Provides interactive guidance when users attempt to exfiltrate sensitive data.
- Policy testing with historical data: Allows testing of new policies on historical data to assess impact before deployment.
- Role-based access control (RBAC): Ensures only authorized individuals can configure policies, view sensitive data, or manage incidents.
- SIEM integration and API support: Integrates with SIEM systems such as Splunk and exposes incidents via API.
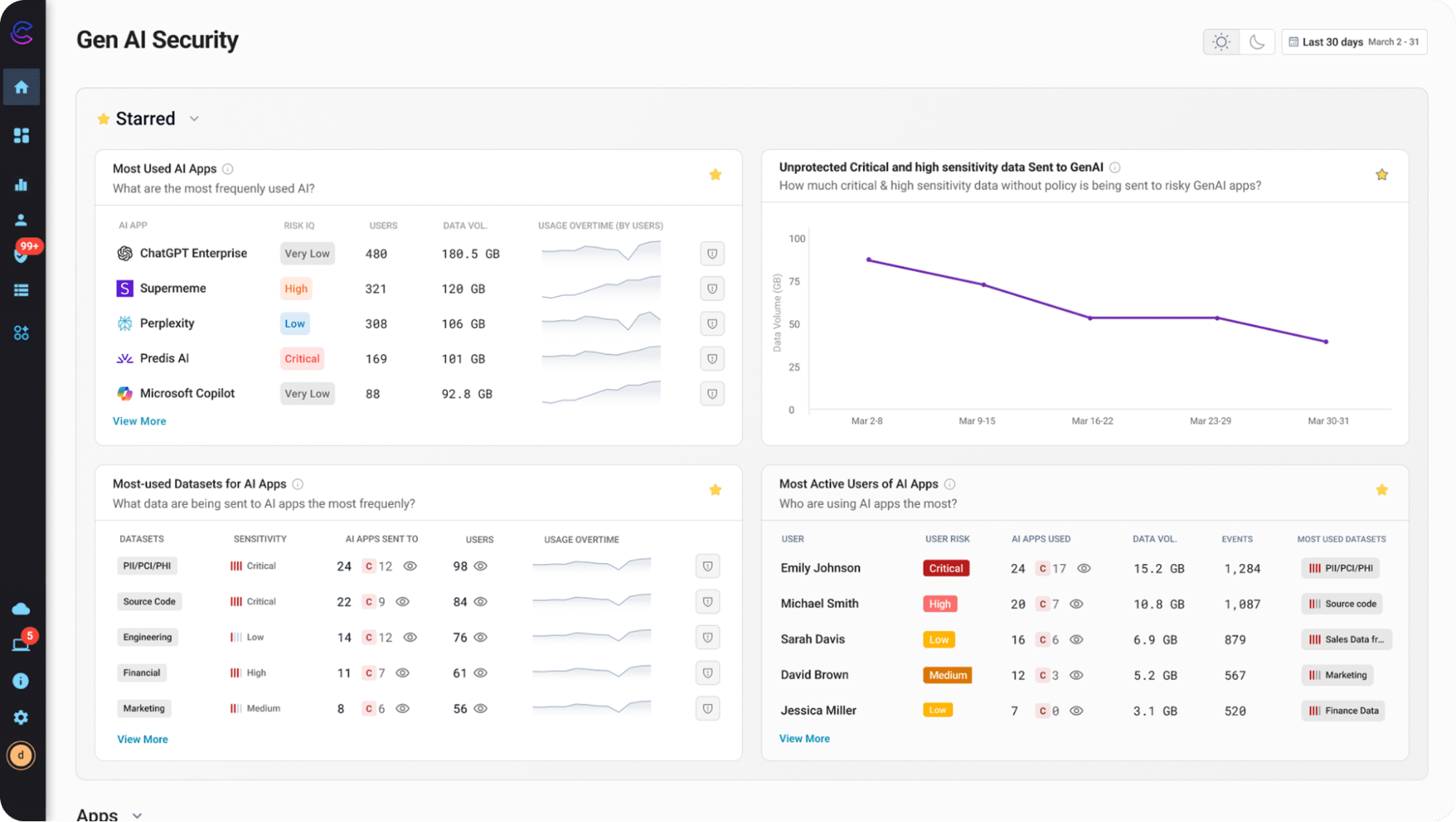
Forcepoint DLP

Forcepoint DLP is a data protection solution offering visibility and control over sensitive information. Through AI-powered automation, it provides monitoring, context-driven policies, and security for cloud and on-premises environments. It also simplifies compliance across over 80 countries with templates and policies for handling PII and PHI.
General features include:
- Data discovery: Scans and classifies both structured and unstructured data across on-premises, cloud, and email systems.
- Monitoring and blocking: Provides continuous monitoring of data interactions and blocks security incidents.
- Compliance templates: Includes pre-configured compliance mandates for over 80 countries.
- Unified DLP management: Centralizes the management of data protection policies across cloud, web, email, and endpoints.
- Behavioral analytics integration: Incorporates user behavior analytics to identify potential insider threats and adapt security measures.
Enterprise features include:
- AI-powered classification: Uses fingerprinting technology and AI-based mesh classification to identify and protect sensitive data.
- Risk-adaptive protection: Uses contextual analysis of user behavior to forecast and mitigate risks.
- Unified incident management: Provides a single interface for managing incidents across data channels.
- Endpoint protection: Extends data protection across endpoints for remote and mobile users.
- Contextual incident reporting: Delivers reports enriched with user activity and data movement analysis.
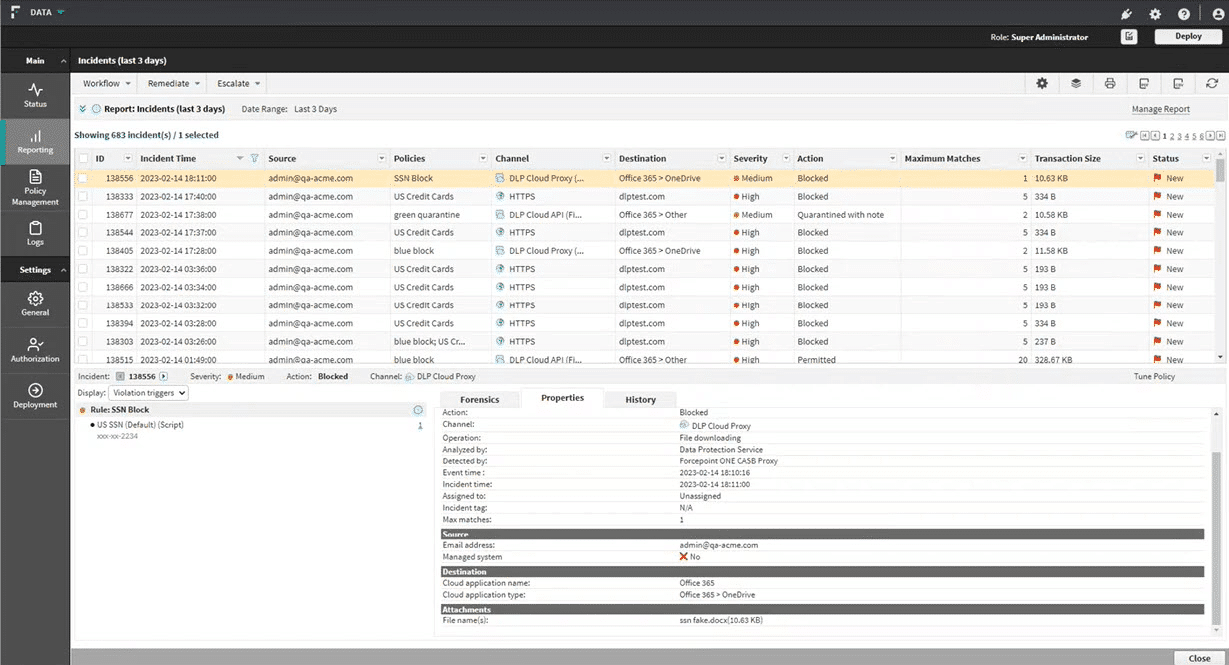
Trellix DLP

Trellix Data Loss Prevention (DLP) offers protection for sensitive data across multiple threat vectors, from endpoints to cloud environments. With its discovery and classification capabilities, it ensures that critical information is monitored, protected, and controlled throughout its lifecycle.
General features include:
- Data discovery and classification: Automatically identifies and classifies sensitive data across various file types.
- Monitoring and event tracking: Continuously monitors data usage and movement.
- Centralized management console: Provides a single console for policy administration, deployment, event monitoring, and reporting.
- Compliance support: Includes pre-configured rules and reporting templates aligned with major regulations.
- User notifications and coaching: Notifies users when they attempt to violate data protection policies.
Enterprise features include:
- Device Control: Prevents unauthorized device installation and ensures content-based monitoring on Windows and macOS.
- DLP Discover: Scans and inventories sensitive data across network storage, databases, and file systems.
- Network Monitor: Provides visibility into data transmitted across networks.
- Network Prevent: Blocks unauthorized data sharing across email and web gateways.
- Incident investigation support: Captures data movement events, aiding forensic analysis with OCR capabilities.
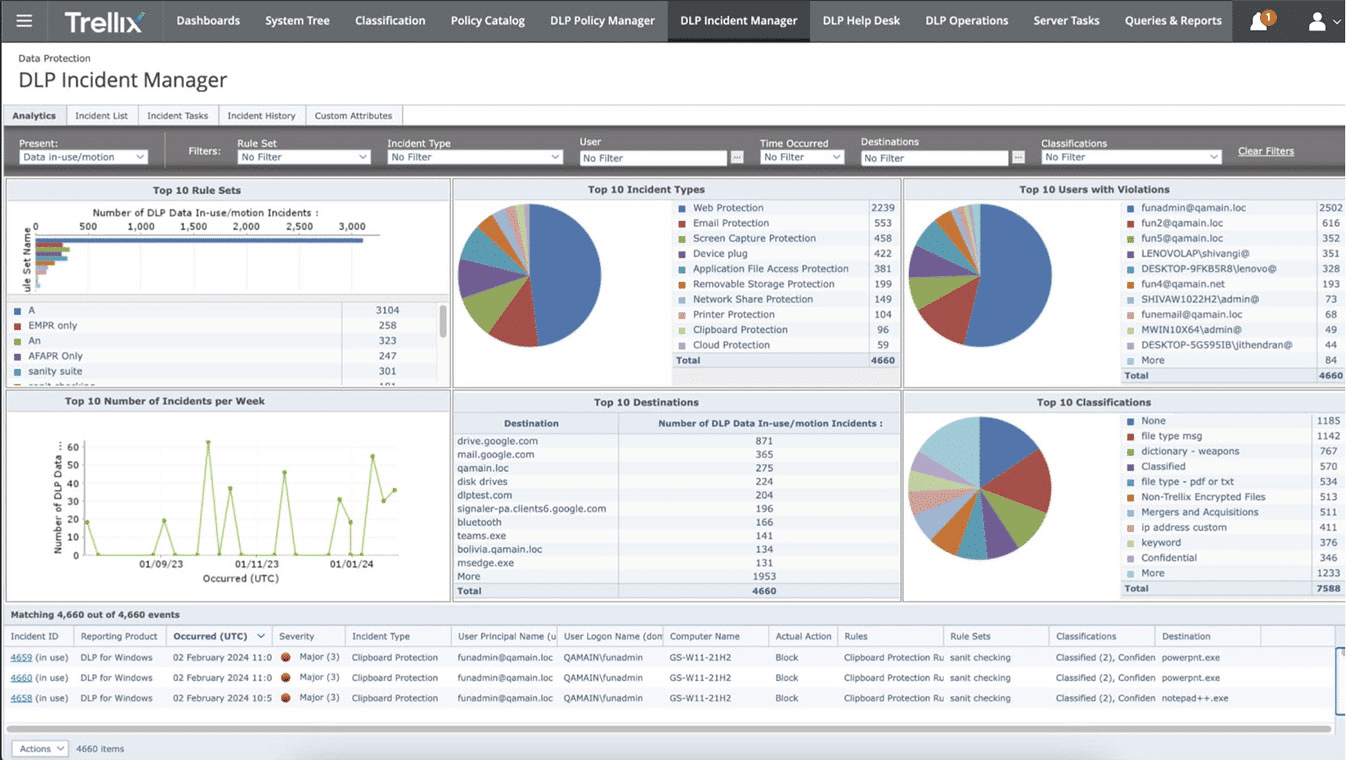
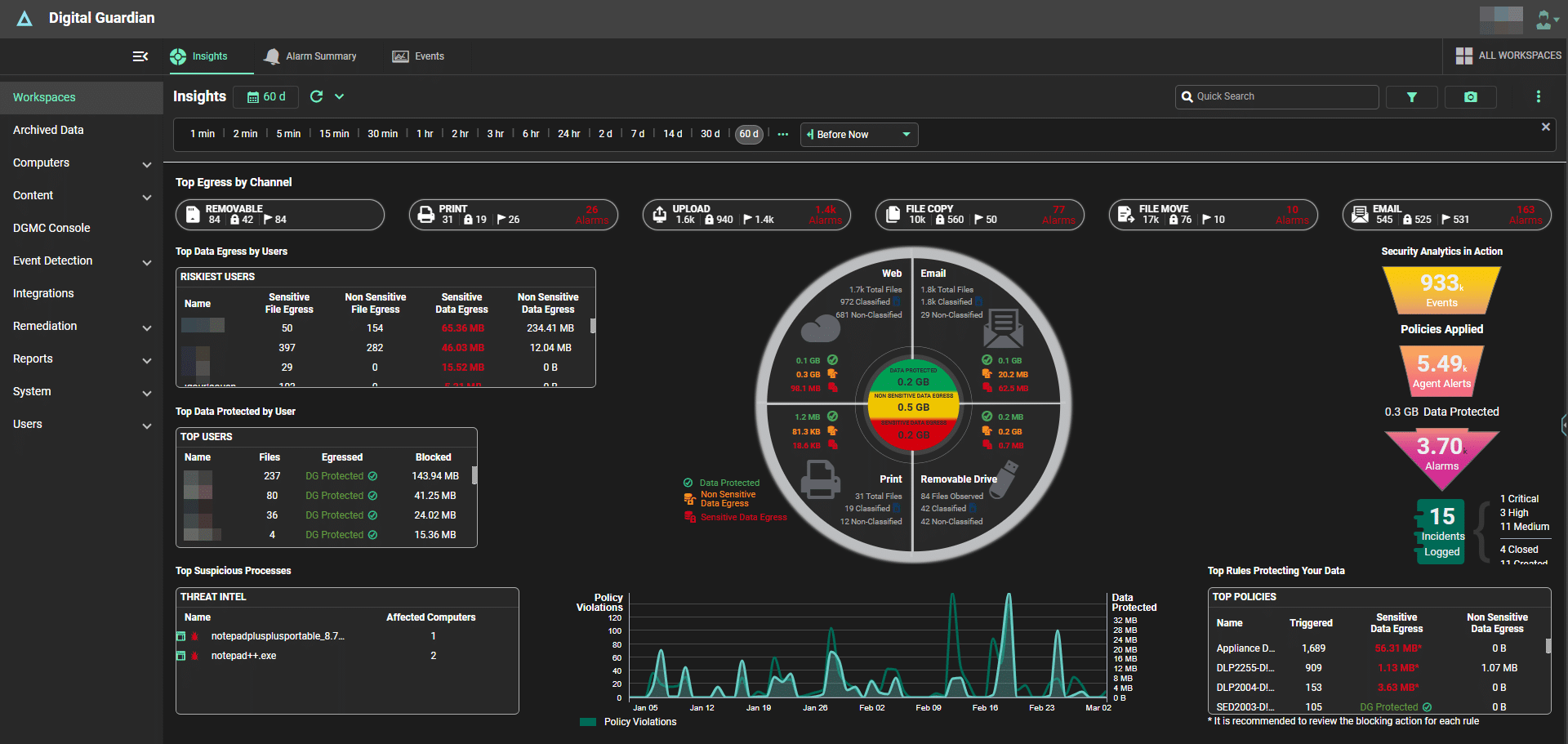
Digital Guardian by Fortra

Digital Guardian provides a DLP solution delivering visibility, protection, and threat detection for sensitive data and intellectual property. The platform supports hybrid environments, securing data across endpoints, cloud applications, and network systems, powered by AWS.
General features include:
- Cloud-delivered SaaS: Offers a SaaS solution on AWS, reducing complexity and overhead.
- Dashboards: Provides out-of-the-box visibility into threats and data egress.
- Threat detection and prevention: Customizable policies with integrations for threat blocking and detection.
- Cross-platform coverage: Supports Windows, macOS, and Linux environments.
- Interoperable with existing security stack: Integrates with data classification tools and security solutions.
Enterprise features include:
- Endpoint DLP: Monitors and records system, user, and data events on endpoints.
- Cloud data protection: Extends DLP to cloud applications and storage with scanning and remediation.
- Data classification: Integrates with classification tools to apply sensitivity labels and policies.
- Data discovery: Identifies and classifies sensitive data at rest across network storage.
- Network DLP: Controls the flow of sensitive data across network, email, and web channels.
Conclusion
Data loss prevention tools have become indispensable for safeguarding sensitive information in today’s distributed, cloud-centric enterprise environments. By providing visibility, control, and enforcement across endpoints, networks, and cloud systems, these solutions help organizations prevent unauthorized access, accidental leaks, and insider threats.

