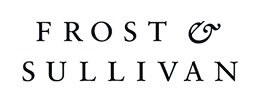Turn Any Traditional or AI Browser into a Secure Enterprise Browser
The Browser Security Platform to protect your data and workforce while they use the browser they love.
Seraphic Named a Leader in the Frost & Sullivan Radar™: Global Zero Trust Browser Security Market, 2025.
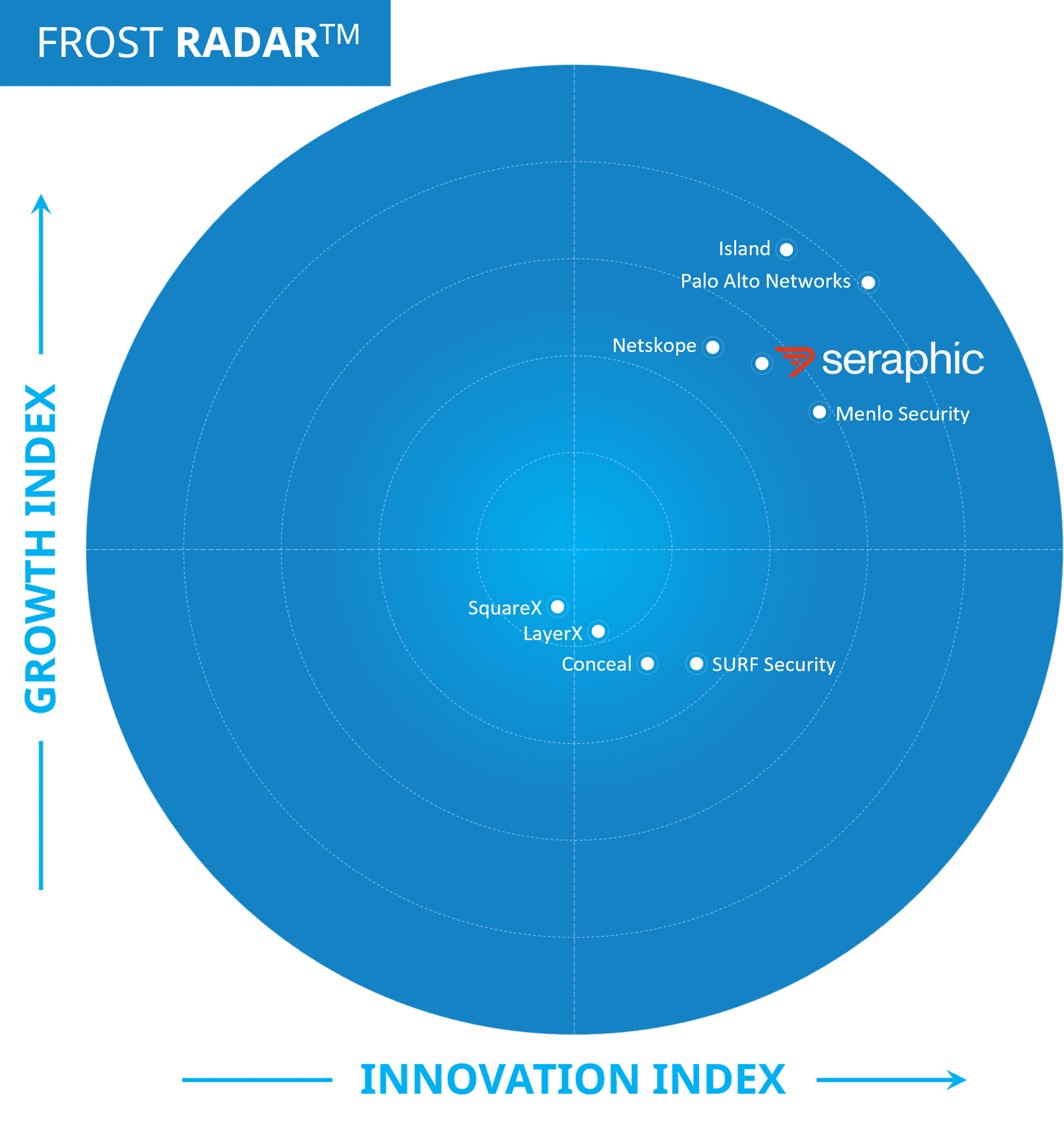
Browser security use cases
Existing solutions – SSE and Extension – lack the necessary visibility & control in the browser.
Protect users & endpoints
Block phishing, malware, and advanced browser-based threats in real time without impacting performance or user experience.
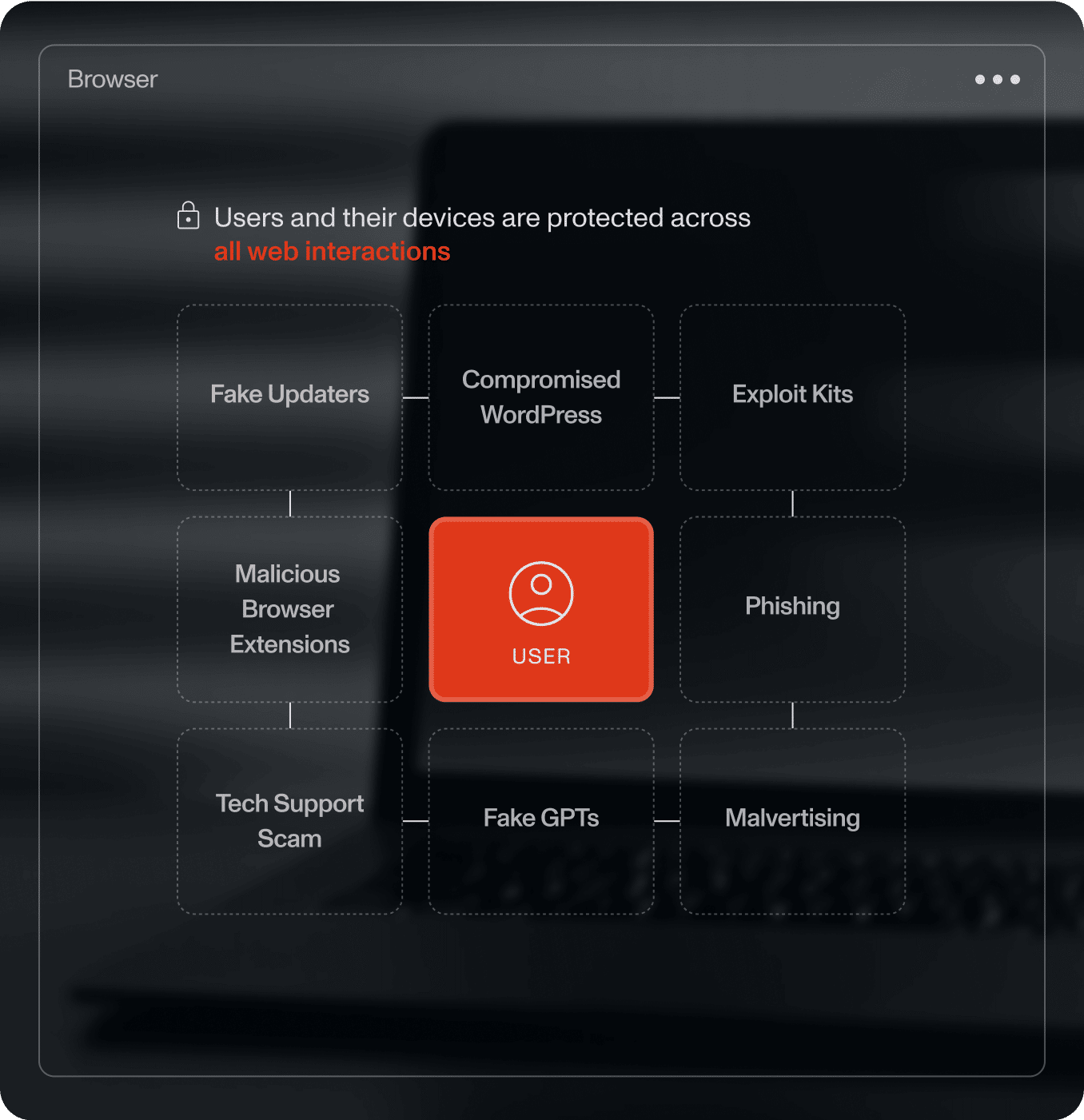
Secure corporate data
Prevent data leakage with granular controls over uploads, downloads, clipboard, screen-sharing, printing, and more, without compromising productivity.
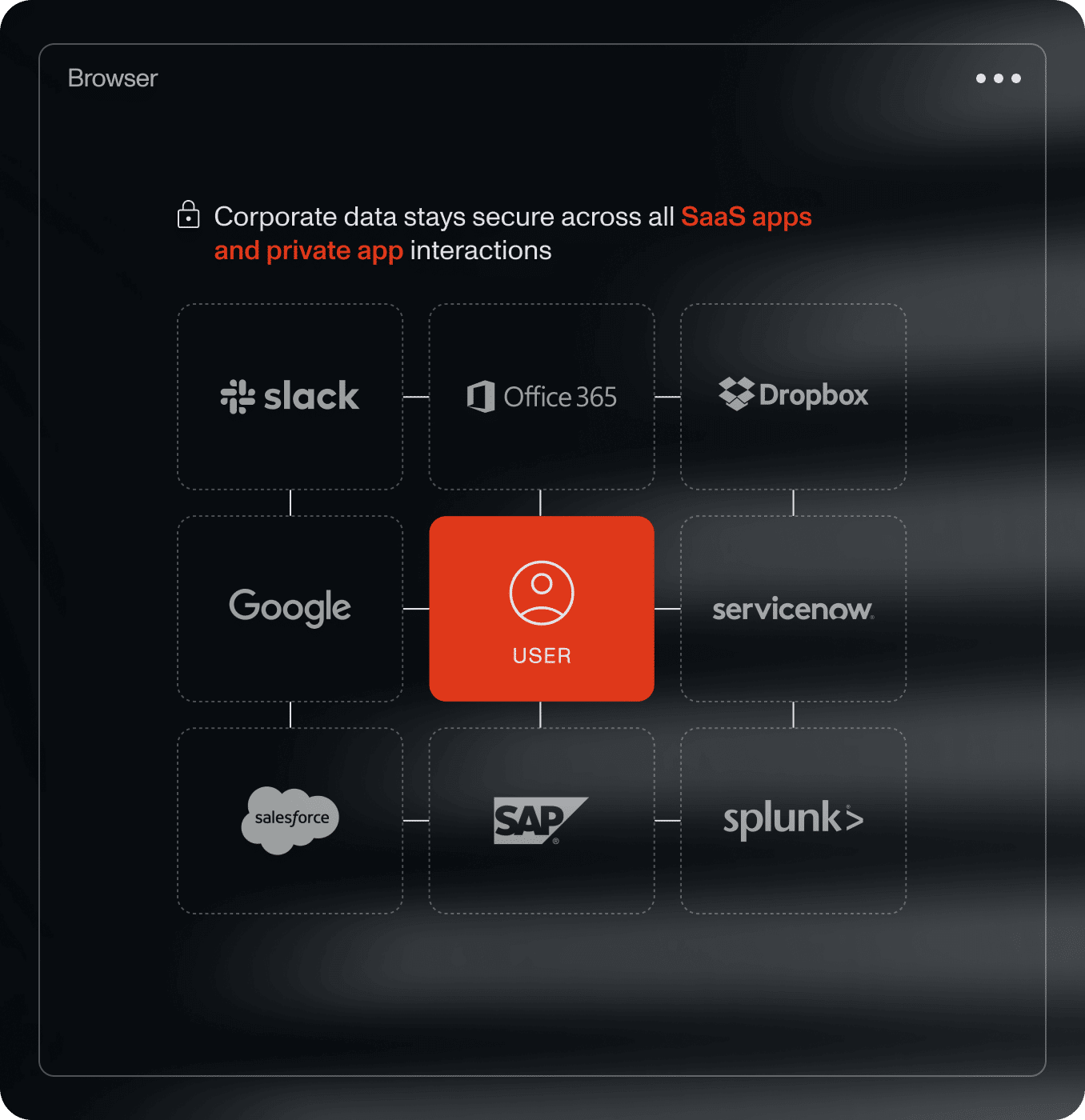
Secure AI adoption
Protect against data leaks, prompt injection, and shadow AI. Seraphic gives you visibility and control over how users and AI tools interact with sensitive data.

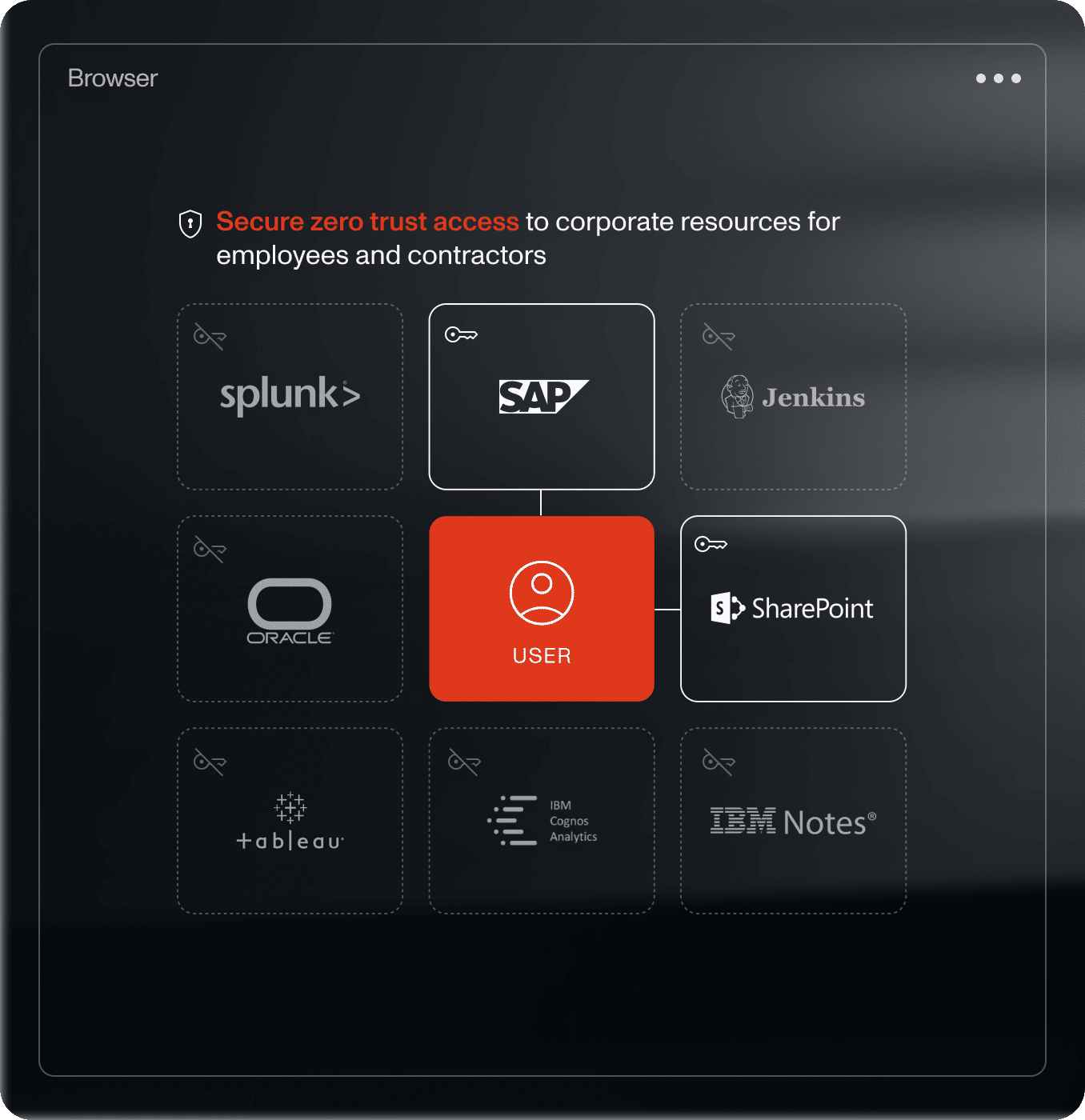
Secure remote access without VPN/VDI
Enable secure access to corporate apps from any location or device without the complexity and cost of traditional VDI or VPN.




What is Seraphic
AI is Revolutionizing Work. We keep you secure while you embrace it.
AI tools and autonomous agents introduce powerful capabilities, but also new risks: data leakage, prompt injection, compliance violation and shadow AI. Seraphic protects your organization at the browser layer, giving CISOs visibility and control over every AI interaction.
AI Visibility
Monitor how employees and AI assistants interact with SaaS, data, private apps, AI tools and identity systems.
AI Access Control
Control what data can be shared with AI tools and which AI tools users can interact with.
Secure AI Enablement
Safely enable AI interactions & workflows with guardrails, full audit trails, and malware prevention.
The first and only solution to
Secure electron-based apps
Seraphic goes beyond browser security to protect Electron-based SaaS desktop applications. Using the same powerful JavaScript-based agent, Seraphic delivers full threat prevention, data protection, and access control – no matter where or how your users work.
Trusted by industry leaders
Jerich Beason
CISO of WM (Waste Management)

Joe Sullivan
Former CSO of Cloudflare, Facebook, Uber

Renee Guttmann
Former CISO of Coca-Cola, Royal Caribbean
Udi Yavo
Former CTO of Fortinet
Uri May
CEO and Co-Founder of Hunters
Elie AbenMoha
CSO of Publicis Groupe
Yaron Slutzki
CISO of Agoda
Haim Inger
CTO of Clal Insurance
Jim Staley
CISO of Verisma
Tyrone Watson-Ferguson
Head of Security Architecture of Burns & McDonnell
Jeff Farinich
CISO of New American Funding
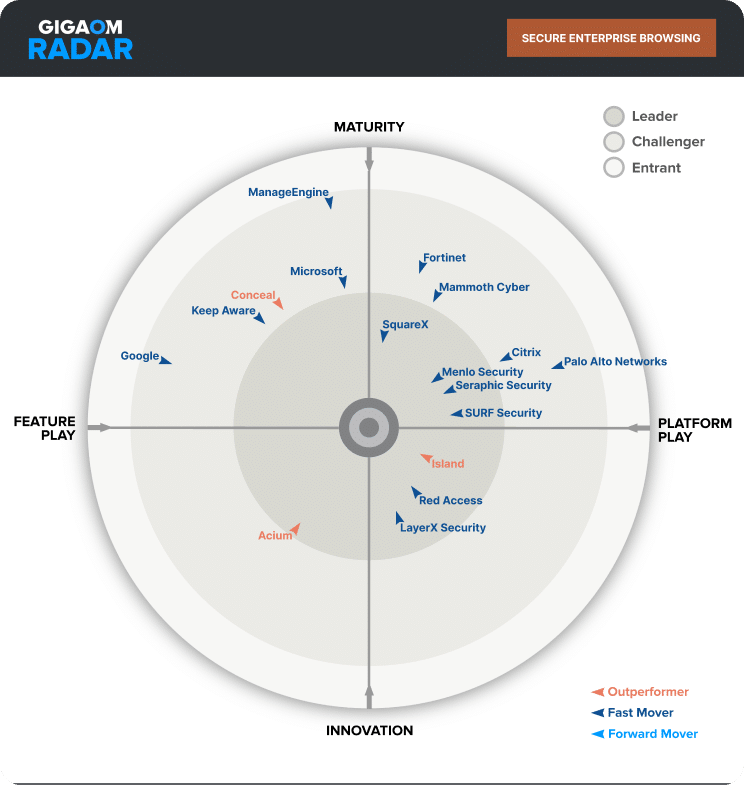
Seraphic Named a Leader and Fast Mover
2025 GigaOm Radar for Secure Enterprise Browsing
Modern work runs in the browser. So do modern attacks.
Today browsers dominate the enterprise
Your employees and contractors use the browser as their gateway to corporate resources, cloud apps, web research, and emerging GenAI platforms.
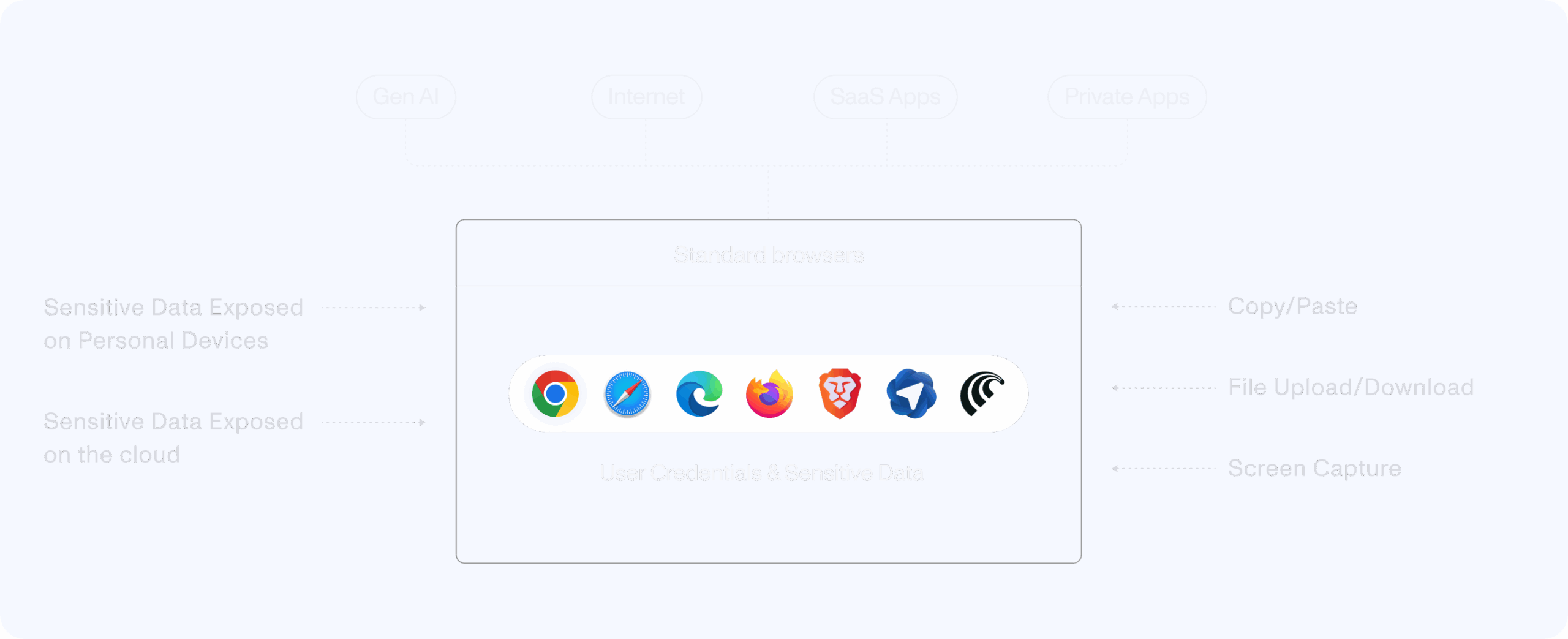
Yet standard browsers are not secured
Main stream browsers – Chrome, Edge, Firefox, Safari- are focused on productivity and lack enterprise-grade security & governance.
Traditional solutions are blind to browser risk
Existing solutions – EDR, SSE and Extension – lack the necessary visibility & control in the browser.
Browsers emerged as a primary attack vector
Attackers are targeting the browser to bypass current defenses and insiders infringe corporate policy and compromise sensitive data.
Think you’re protected?
Major browser security gaps not covered by existing solutions







What is Seraphic
Enterprise browser security on any browser
Single agent
Deploy once to gain full visibility and control across all browser activity, no need for multiple tools or integrations.
Any browser
Protect users across Chrome, Edge, Firefox, Safari and other browsers without forcing a switch or compromising experience.
Any device
Secure access and enforce policy on managed, BYOD, VDI, or third-party endpoints, no matter where users work.
“Long-standing browser vulnerabilities and the rapid integration of AI into browsers have compounded security and privacy risks for organizations.”
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Optimize your security stack
VDI Reduction
VPN Reduction
SSE Reduction
RBI Reduction
Go beyond login
Fuel your SIEM/XDR
Enhance EDR
Complete your SASE strategy


Integrate Seraphic into your security stack
Seraphic seamlessly integrates with your existing security ecosystem to enhance protection, streamline operations, and scale effortlessly across your environment.