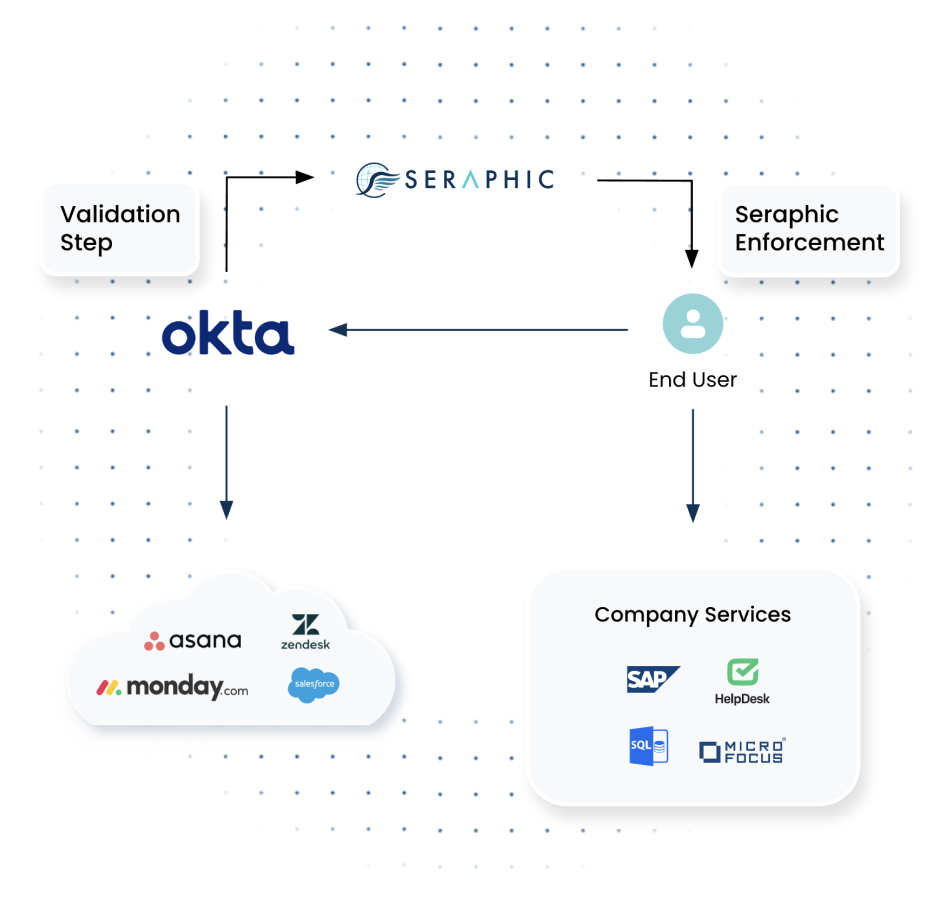
Organizational Application Access
Today, much of your employees’ work is being performed in the browser, whether the application sits in the cloud or in the private data center. These applications allow business continuity, and they allow users to perform their work. These applications also store sensitive corporate data. To ensure the data is not exposed, and there is no risk to business continuity – Seraphic provides protection for these applications on access and throughout the session.
Technical Details
- On access – Seraphic ensures that the user is authenticated successfully, ensures device posture and that the browser is protected with Seraphic.
- Seraphic is added as an additional step in the authorization process inside the identity provider or in the (supporting) SaaS application itself.
- During the session – Seraphic performs ongoing control, allowing users to only perform the actions they should have access to. In addition, Seraphic has a full audit trail of user actions for ongoing monitoring.
- Seraphic also enforces policy controls such as DLP to ensure no sensitive data leaks to unauthorized entities.
- Seraphic can also enforce additional approval (2FA) before performing high-risk actions
- Deployment Vector
- Extension
- Full Proxy injecting Seraphic into sessions