Safe Browsing = Secure Web Browsing
An enterprise-safe browsing solution should protect against two major threat categories:
- Endpoint compromise through browser exploitation and web-based attacks
- User and identity compromise via phishing or the theft of session cookies and tokens
A safe browser for enterprise requires protection that goes beyond consumer-grade anti-malware and anti-phishing features, which rely on signatures and categorization lists that only provide protection against well-known malicious files and URLs.
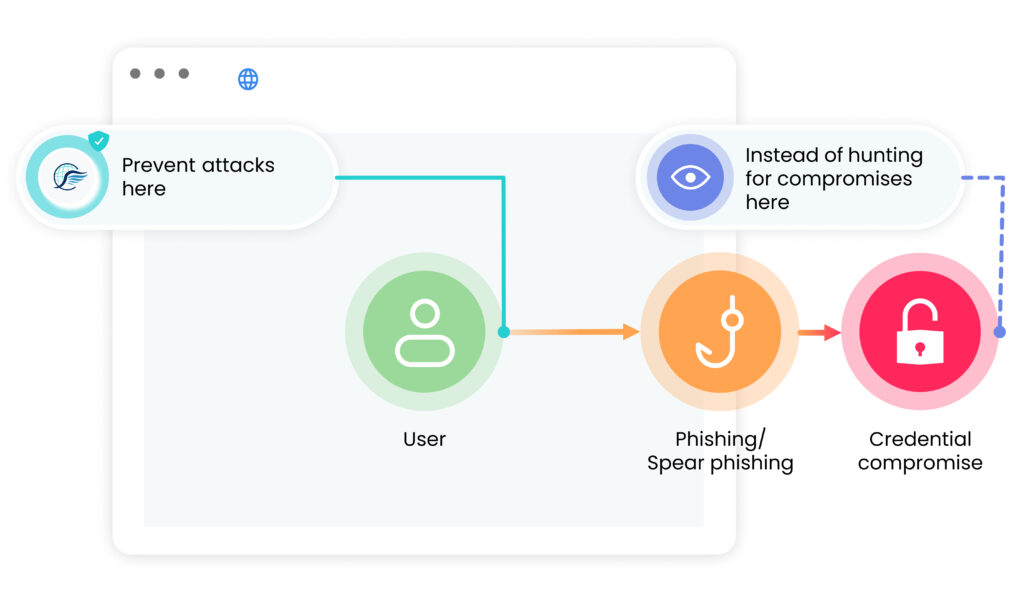
Seraphic’s enterprise browser security takes security even further with advanced protection against zero-day exploits, and other threats.
Enterprise safe web browsing capabilities
Advanced protection features – Exploit prevention that bridges the patch gap
- Is injected directly into the browser runtime, providing protection that other web security tools cannot
- Implements a form of Moving Target Defense (MTD) similar to Address Space Layout Randomization (ASLR) that disrupts exploits without the use of any detection techniques
- Immunizes the browser against memory corruption vulnerabilities that are targeted by the first exploit in the exploit chain

Credential Protection
Phishing is one of the primary techniques adversaries use to gain unauthorized access to enterprise resources. Browsers play a pivotal role in phishing attacks since their success depends on users supplying their credentials to malicious sites. Browsers also store important authentication material such as session cookies and tokens that may be stolen if an adversary successfully compromises a browser.
Seraphic is the only safe browsing solution that protects against 0-hour/ “golden hour” phishing attacks with a unique Detection Engine that:
- Measures and evaluates 200+ runtime parameters to identify malicious sites in real time, without site classification or threat feeds
- Detects and blocks UI redressing attacks such as Browser-in-the-Browser (BitB) and clickjacking that are commonly used on phishing sites
- Is not susceptible to evasion techniques (such as CAPTCHA) that circumvent automated phishing protection tools
Seraphic also guards authentication material used or stored in the browser by:
- Encrypting session cookies and tokens to prevent theft and user impersonation
- Blocking password re-use between different sites or accounts
- Alerting organizations if their users’ credentials have been exposed in a data breach
Web-based Attack Prevention
- Adversary-in-the-Middle (AitM) attacks that can compromise sensitive data
- Attacks used for malware delivery, such as Cross-Site Scripting (XSS), drive-by downloads, and HTML smuggling
- Network scanning (via the browser) that aids attackers in identification of additional targets
- Cryptojacking that consumes compute resources and provides financial resources to threat actors
Enforcing Acceptable Use Policies (AUPs)
Policy Enforcement and Logging
Using Seraphic Security for enterprise safe browsing
- Need safe browsers for the enterprise to protect its hybrid workforce
- Want to avoid major infrastructure and software deployments or modifications
- Are seeking an alternative to browser isolation solutions
Seraphic Security and protects employees and managed devices regardless of whether they are on-premises or remote. Because it works directly in the browser, there is no need for the costly and complex infrastructure that is required by traditional web security solutions. Because it transforms every browser into an enterprise browser, there is no need to force employees to migrate to a new and unfamiliar dedicated browser.
The Safe Browsing Choice for Modern Organizations
Whether you have a hybrid workforce, are looking to minimize infrastructure changes, or seeking an alternative to traditional browser isolation solutions, Seraphic Security is the answer. Our cloud-native security platform transforms any enterprise web browser into a secure, zero-trust environment for safe web browsing.
Take the First Step to Safe Browsing and a More Secure Enterprise





