Security where it matters, inside the browser’s engine
The browser is the new endpoint, and its JavaScript Engine (JSE) is the new OS. Seraphic’s innovative technology provides full visibility and control inside the JSE, delivering capabilities that other security solutions simply can’t.

Innovative technology delivering a full set of capabilities
The browser is the new battleground
Why current solutions are not enough
EPP/EDR
EDRs monitor the operating system, not the browser—leaving blind spots for SaaS usage, web-based data exfiltration, and identity-driven threats that never touch the endpoint. They simply aren’t designed to understand or inspect real-time browser behavior at the user level.
SSE
SSE solutions rely on traffic routing and app integrations—but miss in-browser activity, unmanaged devices, and modern attack techniques like token theft or malicious extensions. Their visibility ends at the network edge, leaving browser-based threats undetected.
Extentions
Browser extensions operate within restricted APIs and can be easily disabled, tampered with, or blocked. They lack the depth and reliability needed for enterprise-grade enforcement, and often fail to detect advanced in-browser threats like token theft or DOM manipulation.
What is Seraphic?
Security built into the browser
Seraphic is an innovative first of it’s kind JavaScript browser agent seamlessly deployed into any existing browser, instantly turning it into a secure enterprise browser.





How Seraphic Works?
01
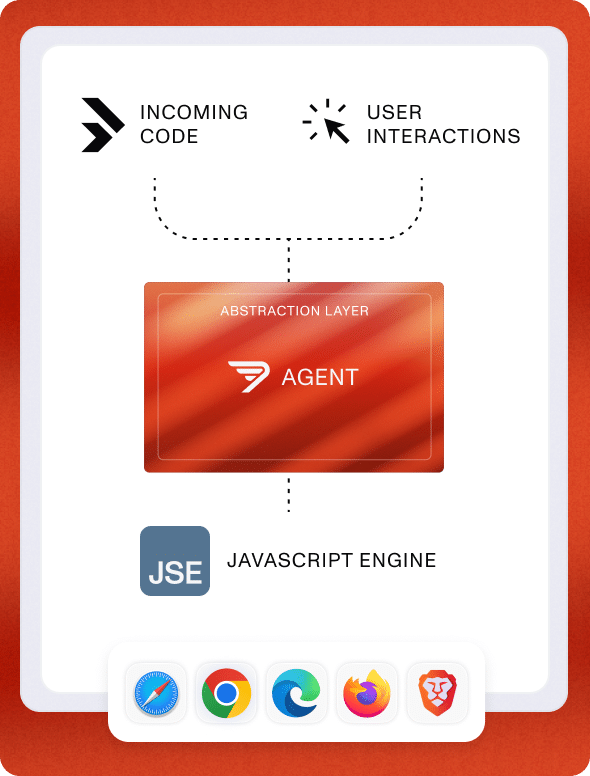
In all browsers, incoming code and user actions are executed directly by the JavaScript Engine (JSE)

02
Seraphic browser agent injected into the browser creating an abstraction layer between those and the browser engine (JSE)
03
The abstraction layer intercepts and controls all browser operations in every session, providing full visibility and control with execution context

Single agent covering corporate, 3rd-party, and mobile devices
corporate devices

Seraphic Enterprise Extension
Seraphic browser agent is seamlessly deployed via lightweight extensions across all browsers. No end-user action or separate endpoint agents required. Delivers consistent browser security and policy enforcement across every browser in use.
3RD party devices

Seraphic Enterprise Browser
Seraphic browser agent is embedded in the user’s preferred browser, enforcing enterprise-grade browser security controls when accessing corporate resources. It creates a secure, isolated workspace for sensitive apps – without impacting user experience or compromising user privacy.
Mobile devices

Seraphic Enterprise Mobile Browser
Seraphic browser agent is embedded in a native mobile browser app or delivered via browser extensions – bring enterprise-grade browser security to both iOS and Android. Users enjoy a familiar browsing experience, while organizations gain visibility and control over sensitive access, even from unmanaged mobile devices.
What makes Seraphic different
Located inside the browser’s engine
Seraphic is the only solution operating in the heart of the browser, the JavaScript Engine (JSE), providing full visibility and control that other solutions are not able to provide.
Detection not dependent on databases & external feeds
Seraphic stops novel, evasive threats by enforcing security in the browser through real-time behavioral analysis—without relying on threat feeds or signatures.
Exploit prevention not based on detection
Rather than relying on previous attack patterns, Seraphic assumes that all code received by the browser, from any source, is untrusted. Seraphic’s prevention engine makes the JSE environment unpredictable and unexploitable, while valid code is executed normally.
Single agent covering all browsers & hidden browsers
Seraphic’s unique technology extends to Electron Framework and other web-enabled applications, ensuring comprehensive protection across diverse application environments while eliminating blind spots in application security to deliver consistent policy enforcement.

Seraphic stops attacks that evade other tools
Seraphic delivers protection before vulnerabilities are discovered, before patches exist, and long before they’re deployed – from zero-day discovery to patch availability to final implementation.
Browser Exploits
Protects against zero-days and unpatched N-days without signatures.
Modern Phishing
Stops sophisticated attacks including AitM phishing like EvilProxy.
Web-based Malware
Blocks drive-by downloads and threats like GootLoader and SocGholish
Shortfalls of other approaches
Extensions shortfalls
Seraphic advantages
Dedicated browsers shortfalls
Seraphic advantages
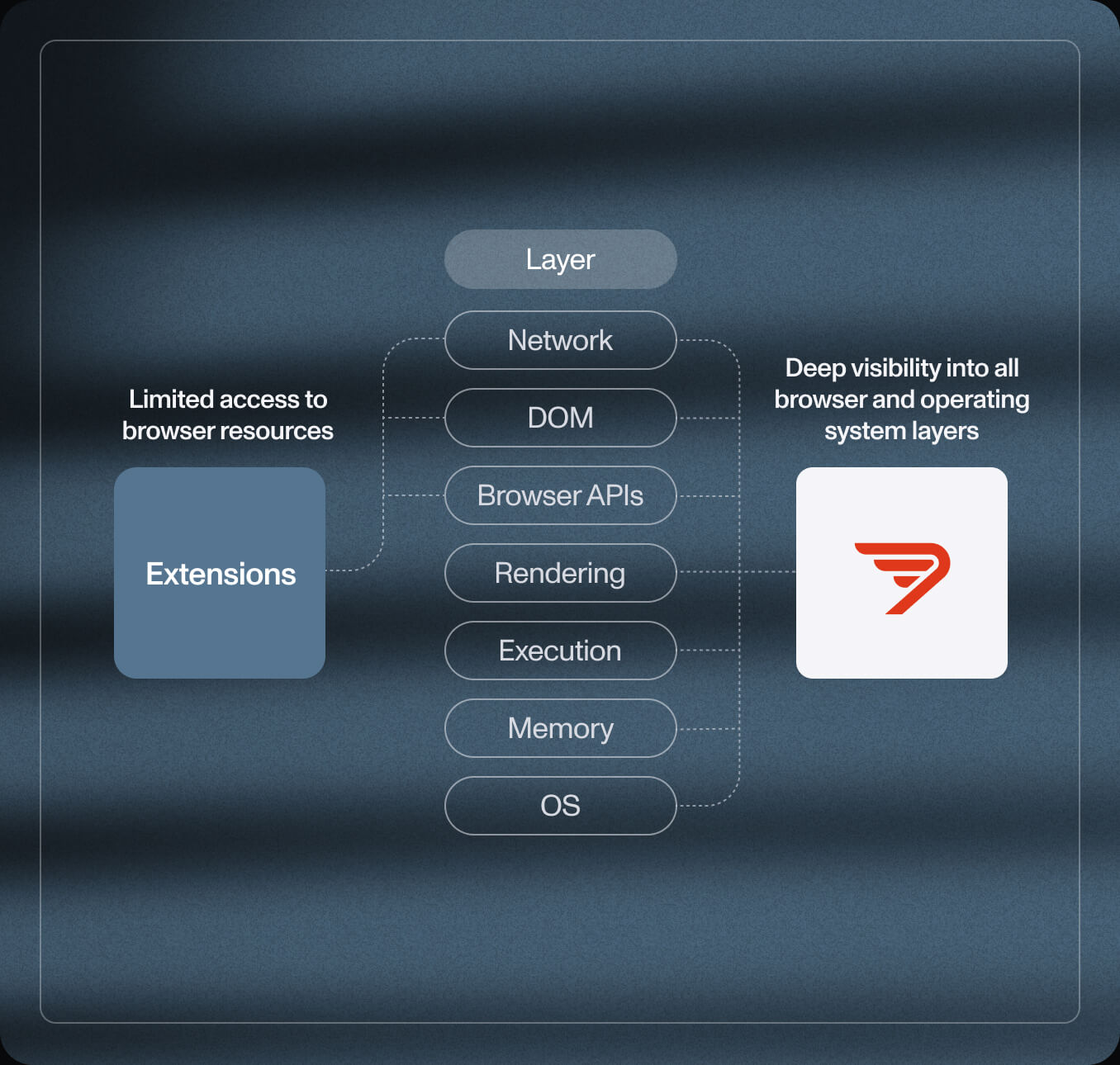
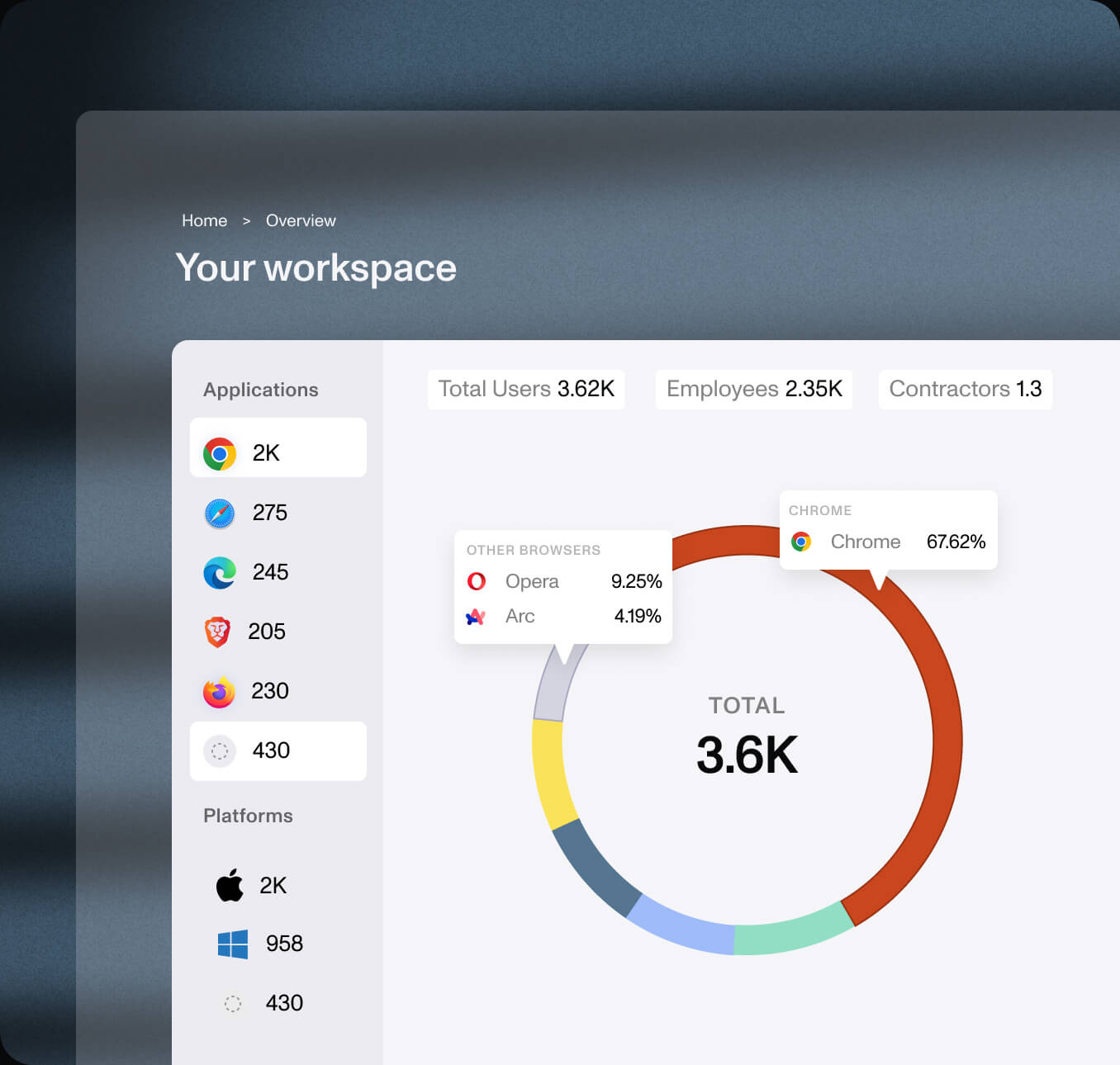
Use cases
Built for the way work happens today
Protect user identities
Protect corporate data & assets
Secure remote access
Enable safe & complaint GenAI usage
Cost & complexity reduction
Built for security teams.
Loved by users.
01
Comprehensive, Real-Time Protection
Stop zero-days, data leaks, malicious extensions, and credential theft before they cause damage. Seraphic enforces security directly at the browser runtime for immediate, proactive threat prevention.
02
Flexibility That Fits Your Stack
Deploy via lightweight extensions, enterprise browsers, or mobile apps — all with consistent policy enforcement and full parity across Chrome, Edge, Safari, Electron apps, and more.
03
Invisible to Users, Effortless for IT
Deliver enterprise-grade protection without clunky agents, browser replacements, or complex infrastructure. Seraphic works in the background, preserving productivity and reducing IT overhead.
04
Consistent Protection on Any Device, Anywhere
Secure every user — whether on a corporate laptop, personal device, or remote desktop — with identity-aware, policy-driven controls that travel with them, without compromising experience.
Extend your security stack to the browser
Seraphic seamlessly integrates with your existing security ecosystem to enhance protection, streamline operations, and scale effortlessly across your environment.




“Most browser security tools create friction for users and are difficult to manage at scale. Seraphic stands out as an invisible, easy-to-use solution that requires no extra training and simply works.”

Take the next step
Subscribe to the newsletter
To see how we are going to use your data see out privacy policy
© 2026 Seraphic ltd. All rights reserved.
Seraphic is now part of CrowdStrike
Protect users, data and AI at the point of access in the browser – Learn more >