What Are Enterprise Browser Tools?
Enterprise browser tools adapt web browsers for business environments, prioritizing security, centralized management, and integration with enterprise systems. They offer features like enhanced security controls, data loss prevention, and support for various enterprise identity systems, enabling secure access to SaaS and private applications.
Enterprise browser tools can take the shape of dedicated enterprise browsers (which require users to switch away from consumer browsers, impacting productivity), or security‑augmented browser tools that integrate with common browsers like Chrome, Edge, and Safari. These tools add features that cater to enterprise‑specific demands such as security, administration, compliance, and user management.
Enterprise browser tools typically offer the following features:
- Enhanced security: Threat prevention, data loss prevention (DLP), and protection against malware and phishing attacks.
- Centralized management: These tools offer centralized control over browser settings, policies, and user access, allowing IT teams to manage and secure Browse activity across the organization.
- Integration with enterprise systems: Enterprise browser tools integrate with identity providers, Single Sign-On (SSO) systems, and other enterprise applications, simplifiing workflows and access management.
- Support for BYOD and remote workforces: They enable secure access to corporate resources from both managed and unmanaged devices, enabling Bring Your Own Device (BYOD) and remote work policies.
- Visibility and reporting: Enterprise browser tools offer improved visibility into user activity and web traffic, providing valuable insights for security monitoring and compliance reporting.
- Privacy and compliance support: They help organizations meet regulatory requirements and protect sensitive data by enforcing privacy policies and compliance standards.
In this article:
Key Features of Enterprise Browser Solutions
Enhanced Security
Enterprise browser solutions are built with security in mind, offering features such as sandboxing, real-time malware detection, phishing protection, and automated patch management. These solutions minimize the attack surface by restricting unauthorized extensions, blocking suspicious URLs, and managing download permissions.
Enhanced security controls help organizations guard against common browser-based threats like credential theft and drive-by downloads, which are frequent entry points for attackers. Security capabilities in enterprise browser tools often include data loss prevention (DLP), isolation of high-risk web sessions, and enforced use of secure connections (HTTPS Everywhere).
Centralized Management
Centralized management is a core feature, allowing IT administrators to deploy, configure, and update browsers across the organization from a single console. This centralization simplifies policy enforcement—such as allowed extensions, homepage settings, network configurations, and bookmark distribution—while ensuring compliance with organizational standards.
Centralized dashboards provide insight into fleet-wide browser status, version control, and potential vulnerabilities. Automated updates reduce inconsistencies and patch security gaps faster, decreasing the organization’s exposure to zero-day exploits. This management approach reduces the manual workload on IT staff and improves consistency across the organization.
Integration with Enterprise Systems
Enterprise browser tools support tight integration with existing IT infrastructure, including identity providers (IdPs), single sign-on (SSO), cloud access security brokers (CASBs), and security information and event management (SIEM) platforms. These integrations enable seamless user authentication, centralized logging, and automated threat detection
Such browser tools often support APIs and connectors for productivity suites, collaboration platforms, and custom applications. This means organizations can enforce policy, monitor usage, or trigger workflows directly from browser activity, granting deeper visibility and control. Integration with enterprise systems also simplifies onboarding and offboarding employees.
Support for BYOD and Remote Workforces
With the rise of Bring Your Own Device (BYOD) policies and distributed teams, enterprise browser tools address the complexities introduced by employees working from various locations and devices. These solutions allow secure access to corporate web applications on unmanaged endpoints while enforcing organizational policies, no matter the device or network.
Support for BYOD ensures that sensitive data stays protected even when accessed from personal hardware. Features like secure containers or browser isolation prevent data leakage and mitigate risks from unsecured networks. Administrators can also revoke access remotely or enforce conditional access policies.
Visibility and Reporting
Advanced reporting features give organizations detailed visibility into web activity, threats, compliance status, and user behavior within the browser. Real-time dashboards and scheduled reports help IT and security teams monitor patterns, identify abnormalities, and take corrective action before issues become incidents.
Reporting tools aggregate and analyze browser data to support incident response, audit trails, and compliance verification. They also provide actionable insights for optimizing web usage, enforcing safe Browse habits, and justifying IT investments. Having granular visibility directly from the browser ensures better governance and faster decision-making for enterprise IT teams.
Privacy and Compliance Support
Enterprise browser tools are designed to support data privacy laws (such as GDPR, CCPA, and HIPAA) by providing settings for data minimization, anonymization, and user consent management. They allow organizations to configure how data is stored, processed, and transmitted through the browser.
These features help ensure that user activity is logged and retained in a way that meets regulatory requirements. Built-in compliance controls provide audit logs, access controls, and breach reporting features tailored for regulated industries.
Notable Enterprise Browser Tools
1. Seraphic

Seraphic Security delivers enterprise-grade browser security that works with employees’ existing browsers, eliminating the need to deploy specialized browsers that require users to change their familiar Browse environments. Seraphic provides a superior remote browser isolation technology that transforms any standard browser into a secure enterprise endpoint without disrupting user workflows or requiring browser migration.
Key features:
- Browser-agnostic security: Works seamlessly with Chrome, Edge, Firefox, Safari, and other browsers, allowing employees to maintain their preferred Browse experience while gaining enterprise protection.
- Complete remote isolation: All web content executes in secure cloud containers, ensuring zero malicious code reaches corporate endpoints, providing stronger isolation than browser-based solutions.
- Transparent deployment: Requires no browser replacement, endpoint agents, or user training, enabling rapid enterprise rollout without the adoption challenges of specialized browsers.
- Universal web compatibility: Supports all web applications, plugins, and interactive content without the compatibility limitations or feature restrictions that can affect standalone enterprise browsers.
- Enhanced user productivity: Preserves native browser performance, extensions, bookmarks, and personalization while adding enterprise security layers invisibly to the user experience.
2. Island Enterprise Browser
The Island Enterprise Browser is a dedicated browser that enables secure Browse for enterprise environments. It allows organizations to manage risks associated with web-based activities. However, it forces users to switch away from existing browsers like Chrome or Safari, which can negatively impact productivity and user satisfaction.
Key features include:
- Universal application access control: Applies conditional access controls based on identity, device, network, location, and application.
- Device visibility and management: Assesses and enforces device posture to ensure compliance with organizational policies, extending management to applications like Zoom, Slack, and Teams.
- Application automation: Automates web application workflows without modifying source code or relying on proprietary APIs.
- Zero trust network access: Strengthens security with zero trust network access, protecting from network and endpoint attacks.
- Built-in security: Protect devices from web-based threats such as malware, phishing, and session hijacking.

Source: Island
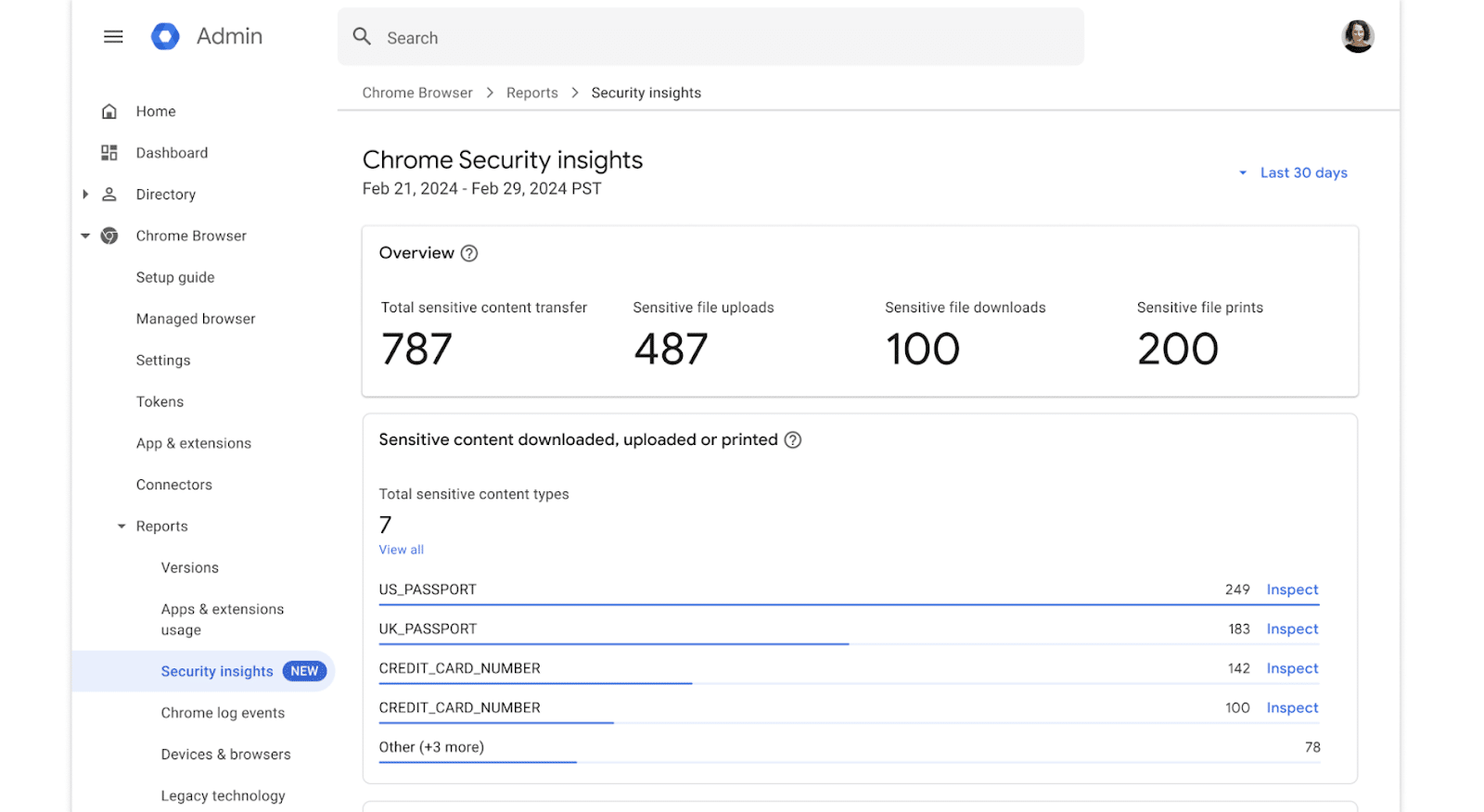
3. Google Chrome Enterprise

Google Chrome Enterprise is a secure browser designed to provide employees with a familiar browser experience. It combines the performance and simplicity of Chrome with additional enterprise-level controls and security features, helping organizations protect their data. However, it offers only basic security functionality compared to dedicated security tools.
Key features include:
- Protection for distributed teams: Scales security protections, management controls, and configurations for distributed teams working across different devices, operating systems, regions, and time zones.
- Simplified management: Centralizes browser management through Chrome Enterprise Core with cloud-based tools for policy enforcement, reporting, and customization.
- Zero trust and data protection: Ensures secure access to company resources with policies that reduce exposure to vulnerabilities.
- Integration with business ecosystems: Chrome integrates with other parts of the IT infrastructure, allowing teams to build an open ecosystem.
Source: Google
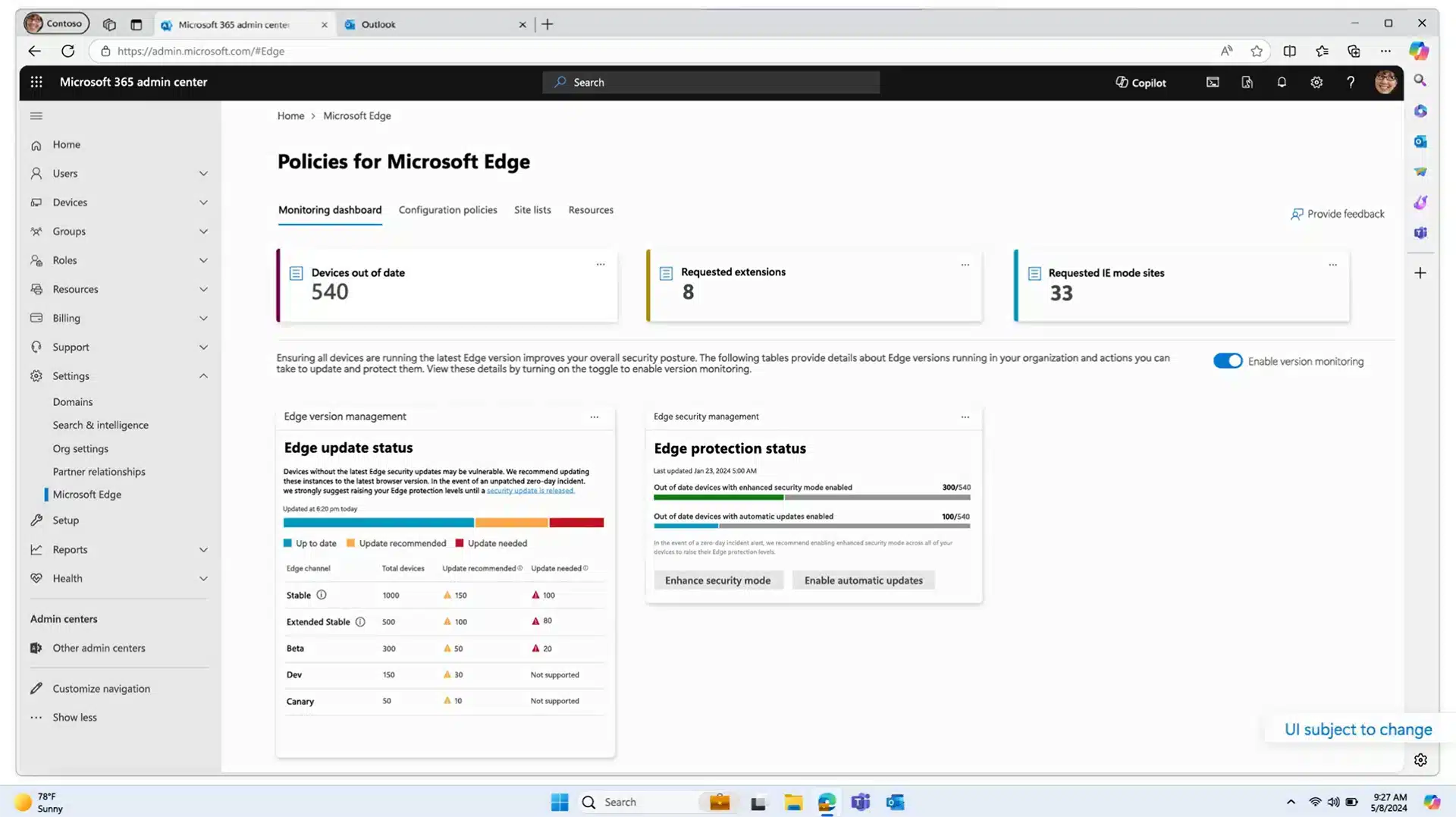
4. Microsoft Edge for Business

Microsoft Edge for Business is a secure enterprise browser intended to improve productivity and simplify workflows while integrating with Microsoft’s security ecosystem. Its features prioritize data protection, security, and management capabilities, ensuring organizations can protect sensitive information across devices.
Key features include:
- Security: Supports zero trust architecture, providing protection against phishing attacks and securing data across devices.
- AI-optimized for productivity: Copilot integration directly into Edge helps simplify workflows by embedding AI capabilities within everyday tasks.
- Simplified browser management: Edge management service offers a guided management experience through the Microsoft 365 admin center.
- Data protection: Protects against data leaks from consumer AI apps on personal devices with data protection controls.
- Integration with Microsoft 365: Native integration with Microsoft 365 tools allows for smooth access to work resources.
Source: Microsoft
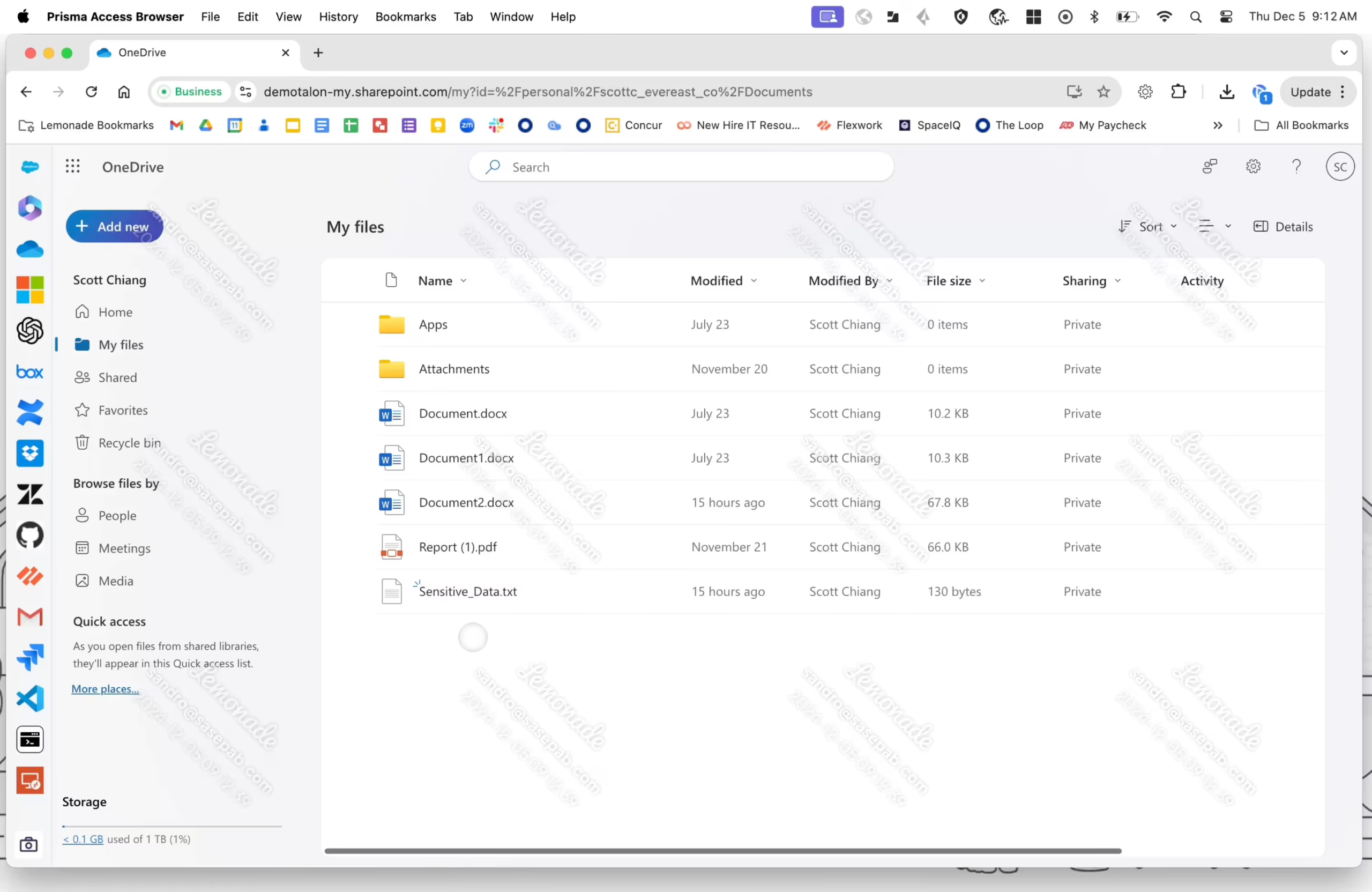
5. Prisma Access Browser

Prisma Access Browser is a dedicated enterprise browser that supports both managed and unmanaged devices. Natively integrated with Secure Access Service Edge (SASE), it ensures organizations have visibility and control over web activity.
Key features include:
- SASE-native security: Integrated with SASE and extends security to all devices.
- Zero trust access: Applies zero trust access policies and data controls to secure corporate data and prevent unauthorized access.
- Threat prevention: Using AI, the browser analyzes events and identifies new threats, blocking malicious files, URLs, and activities.
- Support for BYOD and remote work: Secures work environments on Bring Your Own Device setups.
- VDI reduction: Reduces costs compared to Virtual Desktop Infrastructure solutions.
Source: Palo Alto Networks
Related content: Read our guide to Layerx
Conclusion
Enterprise browser tools have emerged as a critical layer in modern IT security and productivity strategies. By combining advanced security features, centralized management, and seamless integration with enterprise systems, these solutions help organizations protect sensitive data, support remote and BYOD workforces, and maintain compliance in an increasingly complex threat landscape.

