The browser has become the main productivity tool for employees. This is the reason hackers are zeroing in on browsers because employees need to use them to access corporate data, applications, services, and other assets. When you include policy infringements by these employees and increased attacks by those hackers zeroing in, you start to see why the browser has turned into the most serious threat to businesses. Most browsers are built using Chromium (Chrome, Vivaldi, Edge, Brave, etc.), with Mozilla Firefox as the only alternative. This enables bad actors to hyper-focus on vulnerabilities in just two engines.
Why Browser Vulnerabilities Pose Unique Risks
Unlike traditional software applications, browsers serve as the gateway to nearly every aspect of modern business operations. Employees rely on browsers not only for accessing web-based email and productivity suites but also for interacting with sensitive internal applications, cloud platforms, and third-party services. This central role makes browsers an especially attractive target for cybercriminals. A single exploited vulnerability can allow attackers to bypass authentication, steal credentials, inject malicious scripts, or even take control of the entire endpoint. Compounding the risk, many browser vulnerabilities are “zero-day” flaws-meaning they are exploited before a patch is available or widely deployed.
With the average organization using dozens of browser extensions and plugins, each representing a potential weak point, the attack surface grows exponentially. Unlike operating system vulnerabilities, which often require local access or user interaction, browser vulnerabilities can be exploited remotely, often with nothing more than a user visiting a compromised website. This combination of accessibility, centrality, and extensibility makes browser vulnerabilities uniquely dangerous for businesses of all sizes.
The Evolving Tactics of Browser-Based Attacks
Cybercriminals are constantly adapting their methods to exploit browser vulnerabilities more effectively. While early browser attacks often relied on simple phishing or malicious downloads, today’s threat actors employ sophisticated techniques such as drive-by downloads, cross-site scripting (XSS), and man-in-the-browser attacks. These methods can silently compromise a user’s session, steal sensitive information, or manipulate transactions without the user’s knowledge. Attackers also exploit weaknesses in browser extensions, which may have excessive permissions or lack rigorous security reviews.
Furthermore, the rise of “living off the land” attacks-where adversaries use legitimate browser features and APIs for malicious purposes-makes detection even more challenging. For example, attackers may abuse browser autofill features to harvest credentials or leverage WebAssembly to execute malicious code directly in the browser. As organizations increasingly adopt remote and hybrid work models, attackers are also targeting home networks and unmanaged devices, further complicating the security landscape. Staying ahead of these evolving tactics requires not only vigilance but also advanced, adaptive security solutions tailored to the browser environment.
Browser-Based Attacks Are Growing
In his article in Dark Reading, Michael Walter, President, and Co-Founder of Action1 Corporation wrote that “the problem is growing: In the first quarter of 2022 alone, Chrome fixed 113 vulnerabilities, 13% more than in the same period in 2021, while Firefox fixed 88 vulnerabilities, a 12% jump from the first quarter of 2021. These increases make browsers a top target for hackers.”
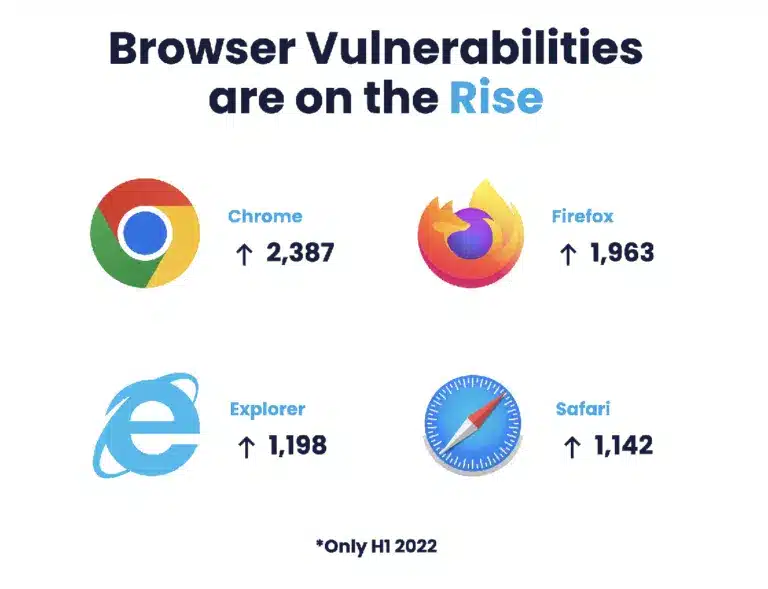
Add to this that phishing is responsible for 90% of data breaches, and 83% of users run versions of Chrome that are vulnerable to zero-day attacks, and you have a recipe for a massive attack surface. Dark Reading’s article gives 4 steps to minimize risk from browser attacks:
- Make sure employees keep all browsers updated
- Enforce multi-factor authentication (MFA) on all critical systems and services
- Regularly clear the browser history on users’ machines
- Roll out an extensive cybersecurity awareness program that educates all your employees.
What the article doesn’t mention is a browser security solution like Seraphic, where you don’t minimize the risk, you eliminate it. Not to say that the 4 steps to minimize risk aren’t great or necessary, they absolutely are, but they require a lot of change management, organizational oversight, and time. Seraphic is complementary to these steps, as it is easy to deploy, easy to operate, and requires 0 change management to secure every browser, on every device, for every user, anywhere they are in the world. And Seraphic does that without replacing your existing browsers. Visit https://seraphicsecurity.com to learn more.