What Is an Enterprise Browser?
An enterprise browser is a browser that provides improved security and compliance for organizational use, beyond what is offered by traditional consumer browsers. There are two main types of enterprise browsers:
- Dedicated enterprise browsers: These are purpose-built applications developed specifically for enterprise use, offering integrated security and IT management features. These browsers often include native support for identity and access management (IAM), secure browsing modes, and built-in compliance tools.
- Security-augmented browsers: These are traditional browsers with additional layers of technology that provide enterprise browser functionality. For example, Seraphic Security creates an abstraction layer between the JavaScript code and JavaScript engine, making the browser unexploitable to threats. Other providers utilize browser extensions to enhance security.
Enterprise browsers cater to the needs of businesses seeking to safeguard sensitive data while facilitating productivity for employees, contractors, and partners. They offer policy enforcement and monitoring capabilities that align with organizational IT strategies.
The demand for enterprise browsers has grown as businesses face rising cybersecurity threats and stricter compliance requirements. This type of browser enables IT teams to implement access controls and threat detection mechanisms directly within the browsing experience.
In this article:
- Key Features of Modern Enterprise Browsers
- Common Use Cases for Enterprise Browsers
- Enterprise Browser vs. Alternative Technologies
- Notable Enterprise Browser Solutions
- Best Practices for Enterprise Browser Management
Key Features of Modern Enterprise Browsers
Security and Threat Prevention Capabilities
Enterprise browsers come equipped with security features designed to prevent cyber threats. They include real-time threat detection, phishing protection, and sandboxing to isolate high-risk activities from sensitive data. These capabilities protect against malware, ransomware, and other threats by restricting access to malicious websites or downloads. Features like granular policy controls allow IT professionals to define user-level restrictions, ensuring corporate data stays safe.
Another significant aspect is encryption for both data in transit and at rest, ensuring information remains secure across networks. Additionally, many enterprise browsers integrate with existing security solutions such as endpoint protection platforms or multi-factor authentication. These integrations create a layered security approach, further reducing vulnerabilities and protecting corporate assets.
Centralized Management and Control
Centralized management is a fundamental feature of enterprise browsers, giving IT administrators control over browser-related activities. Through a unified console, policies can be enforced across devices, from managing browsing restrictions to configuring security settings. This capability simplifies enforcing organization-wide compliance with data protection standards or regulatory requirements.
Furthermore, centralized control allows management of remote users and BYOD policies within the organization. IT teams can remotely update browser settings, restrict plugin usage, or monitor user activity without physical access. This ensures consistency across environments while reducing administrative workloads and helping businesses maintain alignment with security policies.
Integration and Compatibility with Existing Systems
Modern enterprise browsers integrate with corporate infrastructure, improving productivity and security without disrupting workflows. They are compatible with identity and access management (IAM) systems, enabling secure single sign-on (SSO) and user authentication. This ensures employees can access applications and resources without compromising security or convenience.
Additionally, enterprise browsers support integration with security tools such as CASBs (cloud access security brokers), VPNs, and endpoint protection platforms. These integrations strengthen the organization’s defense against cyberattacks while simplifying IT operations.
For dedicated enterprise browsers, organizations need to ensure they are compatible with relevant operating systems and mobile devices. Security-augmented browsers typically run in any environment supported by the base consumer browser.
Enhanced Visibility and Reporting Tools
Enterprise browsers provide visibility and reporting capabilities, enabling IT teams to monitor user activity and detect potential risks. Detailed logs and analytics highlight security incidents, unauthorized access attempts, or policy violations, empowering administrators to respond proactively. Customizable dashboards offer real-time insights, ensuring organizations have the data needed to make informed decisions.
These tools also improve compliance monitoring by tracking interactions with sensitive data or applications. Automated alerts can notify IT teams of suspicious behavior patterns, allowing for quick mitigation actions. By combining visibility with analytics, enterprise browsers transform into vital components of an organization’s risk management strategy.
Privacy and Compliance Support
To meet legislative and regulatory requirements, enterprise browsers offer privacy and compliance features. They support GDPR, HIPAA, and other industry-specific standards by regulating how data is accessed, processed, and shared. Features such as data masking, auditing capabilities, and user activity controls ensure that sensitive data remains protected at all times.
Enterprise browsers also include data loss prevention (DLP) features that prevent unauthorized data access, sharing, and exfiltration. These capabilities enforce policies on clipboard use, screen capture, file uploads and downloads, and printing—helping prevent data leaks through browser activity. For example, administrators can block users from copying sensitive information from a web app or uploading confidential files to unapproved cloud services.
Common Use Cases for Enterprise Browsers
Managing BYOD and Remote Workforce
With the rise of BYOD (bring your own device) policies and remote work, enterprise browsers provide a secure environment for employees accessing corporate resources from personal or unmanaged devices. When BYOD users work with enterprise browsers, it is possible to isolate corporate activity from personal browsing, ensuring sensitive data isn’t exposed to vulnerabilities from non-compliant devices.
For IT administrators, enterprise browsers simplify managing remote workforces. Instead of relying on cumbersome hardware or software installations, they enable direct, secure access via any browser-capable device. This approach reduces complexity while maintaining the necessary controls for data protection and network security.
Protecting Critical Business Applications
Critical business applications, such as CRM or ERP systems, require enhanced protection. Enterprise browsers ensure secure access to these applications through features like app-level restrictions and native integration with IAM systems. By encrypting connections and blocking unauthorized activities, they guard against data leaks or breaches stemming from compromised endpoints.
Additionally, enterprise browsers offer tracking of user interactions within business applications. This visibility allows organizations to detect unusual activity, such as excessive downloads or access outside of approved timeframes. As a result, businesses can protect their most important assets and ensure continued operational resilience.
Zero Trust Security Implementation
Enterprise browsers enable zero trust security strategies by ensuring all users, devices, and applications must be authenticated and authorized. Through features such as device verification, real-time activity monitoring, and enforced least-privilege policies, these browsers maintain control over network access. This zero trust approach eliminates implicit trust and mitigates risks from internal and external threats.
By integrating with zero trust frameworks, enterprise browsers provide organizations with a dynamic and adaptable cybersecurity posture. Continuous monitoring ensures that potential threats are detected and neutralized before they escalate. This makes them invaluable tools for enterprises aiming to adopt zero trust principles without disrupting their existing infrastructure.
Secure Access for Contractors and Partners
Enterprise browsers help organizations securely extend access to contractors and business partners without risking sensitive information. When granting access to an organization’s internal systems, ensuring third parties use enterprise browsers can enforce security protocols such as restricted site access, data exfiltration prevention, and activity monitoring. Contractors can only access approved resources, minimizing exposure to potential breaches.
Additionally, these browsers allow IT teams to set up temporary or role-based access permissions, ensuring that external collaborators operate within predetermined boundaries. At the end of their contracts, permissions can easily be revoked without the lingering risk of unauthorized access, ensuring continued data protection.
Enterprise Browser vs. Alternative Technologies
Let’s contrast enterprise browsers with three alternative technologies that can offer similar security and compliance capabilities, but each has its pros and cons.
Enterprise Browser vs. Virtual Desktop Infrastructure (VDI)
Virtual desktop infrastructure (VDI) delivers a full desktop experience from a centralized server, requiring significant backend infrastructure and maintenance. Enterprise browsers, by contrast, offer a lightweight alternative focused on securing access to web-based applications and resources without the overhead of managing entire virtual desktops.
VDI is often used for legacy applications or when full desktop control is required, but it introduces latency and user experience challenges, especially over unstable networks. Enterprise browsers avoid this by operating natively on the endpoint, providing faster performance and smoother user experience, while still enforcing access policies and isolating corporate data.
Cost and complexity are also key differentiators. VDI typically demands higher capital and operational investment due to licensing, server provisioning, and IT management. Enterprise browsers reduce these burdens by offering centralized policy management without needing to virtualize the entire operating system.
Enterprise Browser vs. Remote Browser Isolation (RBI)
Remote browser isolation (RBI) separates browsing activity from the endpoint by rendering web content in a cloud or isolated environment, then streaming a sanitized version to the user. This prevents web-based threats from reaching the local device but can degrade performance and limit interactivity.
Enterprise browsers achieve many of the same isolation benefits through local sandboxing and granular access controls, without the need to proxy or virtualize the browsing session. This approach allows for native application performance, better user experience, and compatibility with modern web technologies.
While RBI is effective for high-risk browsing scenarios (e.g., unknown URLs or public internet access), enterprise browsers provide broader value by integrating with IAM tools, enforcing enterprise policies, and offering visibility into user behavior—all within a familiar browser interface.
Enterprise Browser vs. Secure Access Service Edge (SASE)
Secure access service edge (SASE) is a network architecture that combines WAN capabilities with cloud-delivered security services like secure web gateways, CASBs, and ZTNA. It focuses on securing all network traffic, not just browser activity.
Enterprise browsers complement SASE rather than compete with it. While SASE secures network pathways, enterprise browsers provide endpoint-level control and visibility into application use, user actions, and browser-based threats. This endpoint perspective is critical for organizations implementing zero trust models.
Unlike SASE, which often requires network rerouting and complex integration, enterprise browsers offer a faster deployment path. They secure access at the application layer, which is ideal for organizations that rely heavily on SaaS or need to manage access from unmanaged devices without deploying full SASE stacks.
Notable Enterprise Browser Solutions
Security-Augmented Browsers
1. Seraphic Security

Seraphic Security delivers enterprise-grade browser security that works with employees’ existing browsers, eliminating the need to deploy specialized browsers that require users to change their familiar browsing environments. Seraphic provides a superior remote browser isolation technology that transforms any standard browser into a secure enterprise endpoint without disrupting user workflows or requiring browser migration.
Key features:
- Browser-agnostic security: Works seamlessly with Chrome, Edge, Firefox, Safari, and other browsers, allowing employees to maintain their preferred browsing experience while gaining enterprise protection.
- Complete remote isolation: All web content executes in secure cloud containers, ensuring zero malicious code reaches corporate endpoints, providing stronger isolation than browser-based solutions.
- Transparent deployment: Requires no browser replacement, endpoint agents, or user training, enabling rapid enterprise rollout without the adoption challenges of specialized browsers.
- Universal web compatibility: Supports all web applications, plugins, and interactive content without the compatibility limitations or feature restrictions that can affect standalone enterprise browsers.
- Enhanced user productivity: Preserves native browser performance, extensions, bookmarks, and personalization while adding enterprise security layers invisibly to the user experience.
2. LayerX

LayerX is an enterprise browser extension platform that transforms the browser into a policy-enforced security endpoint. Unlike traditional browser security tools or standalone enterprise browsers, LayerX integrates into existing browser environments without requiring users to change their workflows.
Key features include:
- Agentless, browser-agnostic deployment: Installs as an extension on a browser (e.g., Chrome, Edge, Firefox), without needing a dedicated browser or changing user preferences. Compatible with MDM and SSO/IdP tools.
- Web & SaaS DLP: Detects and blocks unauthorized uploads, file sharing, and risky user behavior in web and SaaS environments.
- GenAI security controls: Identifies and governs the usage of generative AI tools across the enterprise, preventing accidental data exposure and mitigating shadow AI risks.
- Shadow SaaS discovery and control: Detects unsanctioned SaaS app usage (“shadow SaaS”) and enables control over access and interactions.
- Protection from risky browser extensions: Automatically identifies malicious or risky browser extensions installed by users and enforces policies to block or limit their impact.
Limitations (according to users on Gartner):
- Limited to environments where browser extensions are allowed; blocked in hardened systems.
- Browser extension model may lack the deep system-level control of dedicated enterprise browsers.
- Effectiveness depends on the proper configuration of IAM and MDM platforms; misconfigurations reduce visibility and enforcement.
Source: LayerX
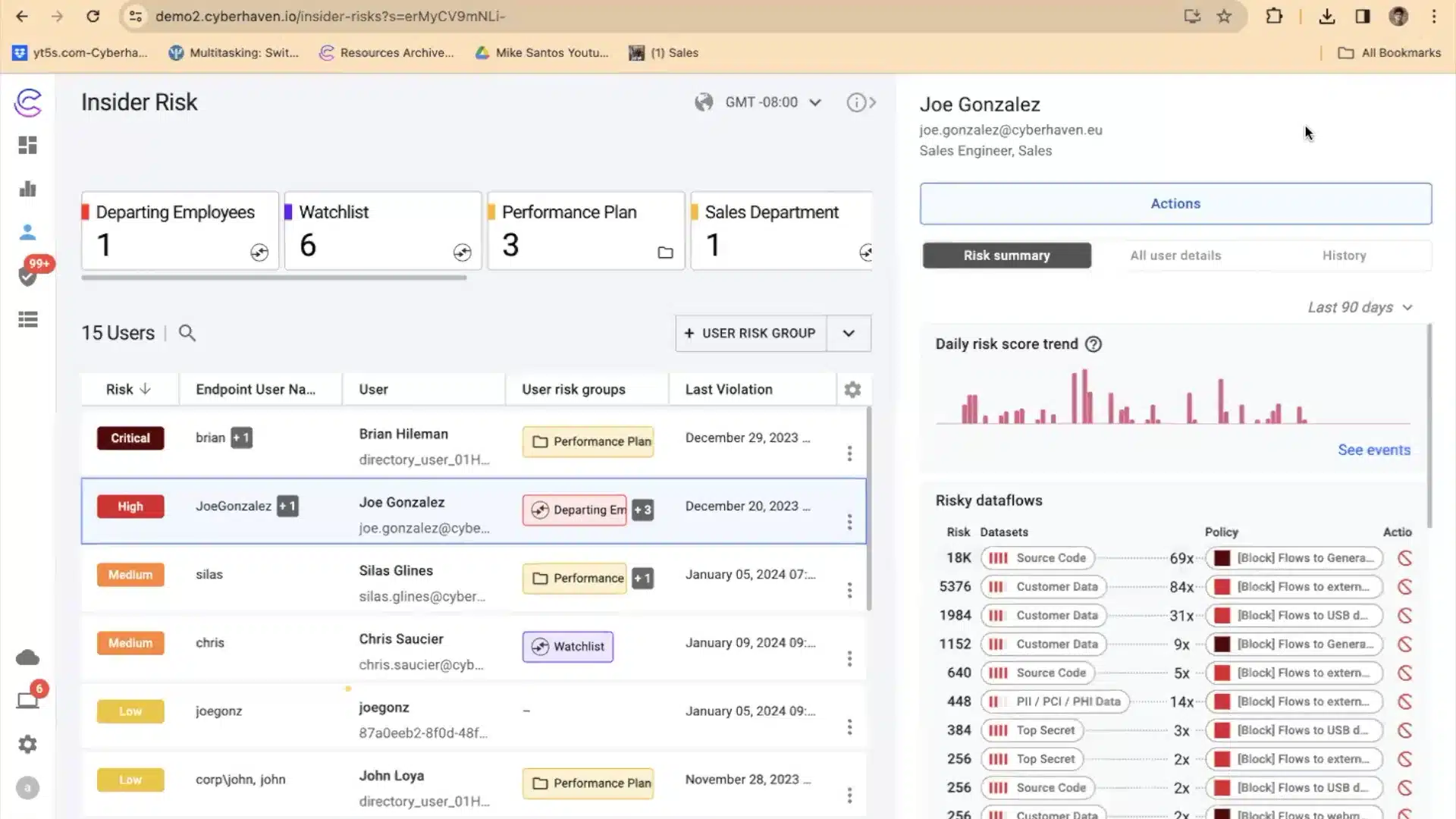
3. Cyberhaven

Cyberhaven is a data security platform that introduces data detection and response (DDR). Instead of relying on content patterns to classify sensitive data, Cyberhaven uses data lineage to trace how data is created, modified, and shared. This allows organizations to understand the context behind every piece of information and protect it.
Key features include:
- Data lineage classification: Tracks the history of data objects, from the point of origin through every move, copy, and transformation.
- Billions of event correlations: Automatically analyzes large amounts of event data to reconstruct each file’s journey.
- Multi-mode deployment: Offers three lightweight and complementary deployment options—endpoint agent, browser extension, and cloud API connectors.
- Cloud API connectors: Integrates with cloud platforms like Google Workspace and Microsoft 365 to provide visibility into native cloud activity, including data access from unmanaged devices.
- Browser extension coverage: Captures web activity on major browsers to fill visibility gaps left by network-based solutions, especially for SaaS and web-based applications.
Limitations (according to users on G2):
- Requires widespread deployment across endpoints, browsers, and cloud services for full data visibility.
- Data lineage analysis may impact system performance in high-volume environments.
- Full functionality often requires integration with SIEM or existing data platforms.
Source: Cyberhaven
Dedicated Enterprise Browsers
4. Island Browser

Island Browser is an enterprise browser delivering secure, controlled, and optimized web access for work environments. It embeds security, access management, and productivity features into the browsing experience, enabling organizations to enforce zero trust policies, reduce reliance on legacy infrastructure like VDI, and provide safe BYOD access.
Key features include:
- Universal application access control: Applies granular, condition-based access policies based on identity, device posture, network, or location.
- Device visibility and management: Helps continuously assess and manage device compliance, including for applications beyond the browser like Slack, Teams, or WhatsApp.
- Built-in zero trust network access: Secures private app access without needing external agents or VPNs.
- Browser-native security: Defends against malware, phishing, session hijacking, and other browser-level threats with embedded security features.
- Context-aware data protection: Enforces dynamic data policies that adapt to user behavior and risk context, helping prevent data loss and misuse.
Limitations (according to users on Gartner):
- May require significant change management due to the need to replace existing browsers.
- Compatibility issues are reported with some legacy or niche web applications.
- Ecosystem maturity is still developing, with limited community and third-party support.

Source: Island
5. Prisma Access Browser
Prisma Access Browser is a cloud-native browser built into Palo Alto Networks’ SASE platform. It extends zero trust protection and visibility to both managed and unmanaged devices without adding friction to the user experience. It eliminates the need for complex workarounds like VDI or third-party agents.
Key features include:
- SASE-native integration: Delivers security from the inside out by natively extending SASE controls to browser sessions.
- Zero trust access controls: Enforces zero trust principles through contextual access policies that evaluate user identity, device posture, and activity.
- Granular data protection: Supports browser-level controls such as copy/paste restrictions, screenshot blocking, watermarking, and session recording.
- GenAI risk management: Offers visibility over the usage of generative AI tools, helping prevent shadow AI risks and protect information shared with public AI models.
- High-performance secure workspace: Combines lightweight deployment with a native app-like user experience.
Limitations (according to users on Peerspot):
- Best suited for organizations already using Palo Alto Networks; limited integration outside the ecosystem.
- Cloud-native design may raise compliance or data sovereignty concerns in regulated industries.
- Performance relies on strong and stable network connectivity.
Source: Palo Alto Networks
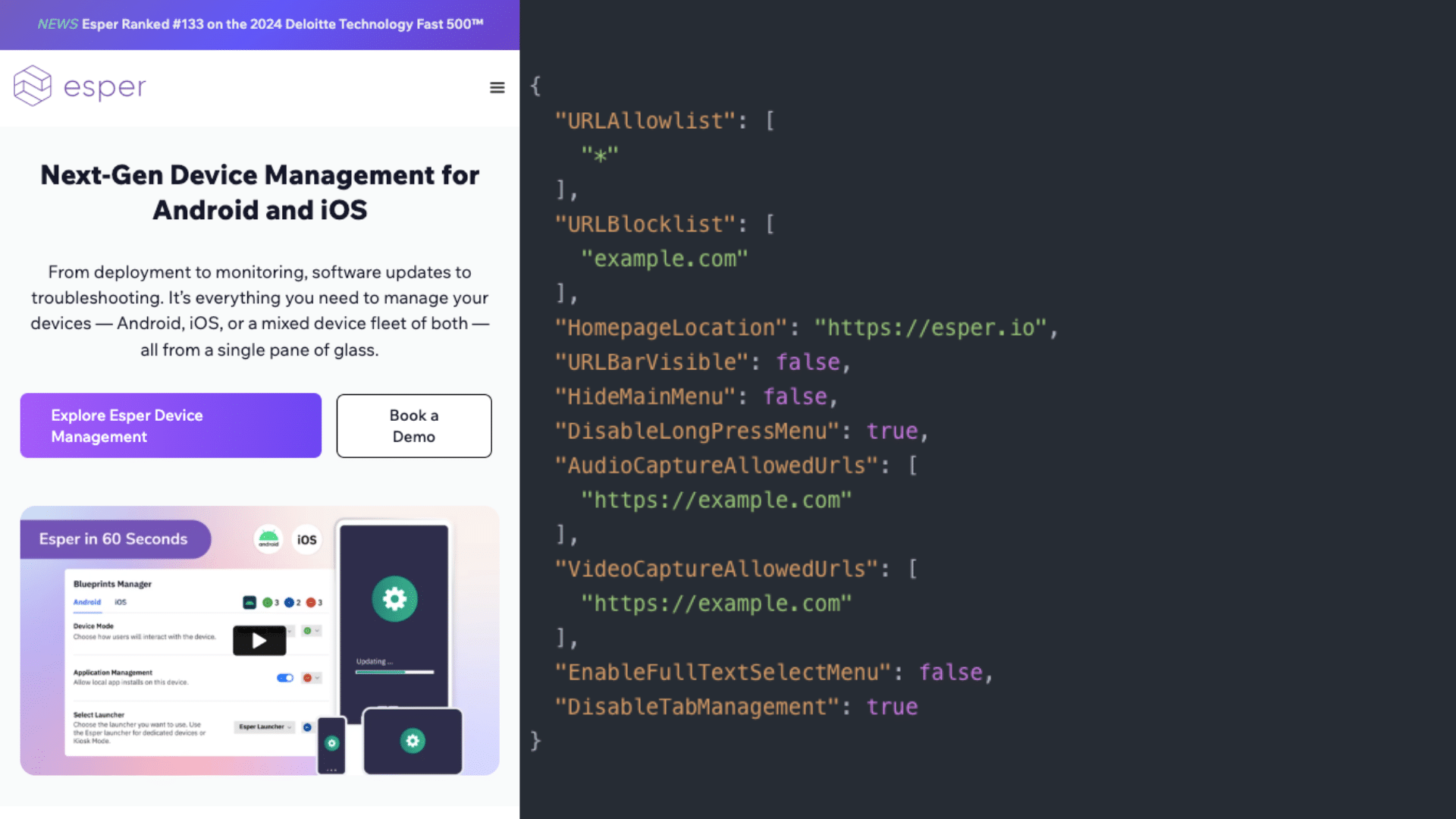
6. Esper Titanium
Esper Titanium is designed as a hardened enterprise browser offering full control over the web experience in critical environments. It emphasizes unbreakable security by integrating custom OS-level protections with a tightly managed browser.
Key features include:
- System-level hardening: Built on a custom Android OS stack that eliminates standard attack vectors, making exploitation more difficult.
- Minimalist architecture: Reduces system complexity and external dependencies, narrowing the potential attack surface.
- Integrated enterprise control: Offers fine-grained access policies, app allowlisting, and restriction of browser functions like printing or screenshotting.
- Purpose-built for enterprise deployment: Designed for kiosk, frontline, and shared device environments, where maximum control and reliability are required.
Limitations (according to users on Getapp):
- Limited to Android environments; not compatible with Windows or iOS.
- Custom OS stack requires specialized maintenance and support.
- Not ideal for general-purpose or knowledge worker use cases.
Source: Esper
7. Microsoft Edge for Business

Microsoft Edge for Business is the enterprise-focused version of the Edge browser, offering more advanced security, compliance, and management capabilities for corporate users.
Key features include:
- Separation of personal and work profiles: Allows for logical separation of data and policies, supporting compliance and BYOD strategies.
- Policy management through Microsoft Endpoint Manager: Enables central configuration of security settings, extensions, and browsing behavior via Microsoft Intune.
- Native integration with Microsoft 365 and Azure AD: Supports seamless SSO and access control with enterprise applications.
- Security enhancements: Includes hardware isolation, SmartScreen, and Defender Application Guard for malware and phishing protection.
Limitations (according to users on Gartner):
- Deep integration with Microsoft tools reduces flexibility for non-Microsoft environments.
- Depends on Intune and other Windows-centric tools for policy management.
- Privacy features may need additional configuration to meet stricter corporate governance standards.
Source: Microsoft
8. Citrix Enterprise Browser
Citrix Enterprise Browser is part of the Citrix Secure Private Access suite. It provides secure access to SaaS and web apps, especially for unmanaged and BYOD devices, by combining application-level controls with browser-based isolation.
Key features include:
- Browser-based zero trust access: Delivers secure, isolated access to internal and SaaS apps, without requiring a VPN or full desktop virtualization.
- Granular policy enforcement: Supports copy/paste restrictions, watermarking, keystroke logging prevention, and data download controls.
- Cloud-native management: Allows centralized policy control, auditing, and session management through the Citrix cloud console.
- User experience preservation: Maintains a high-performance experience while enforcing security policies transparently in the background.
Limitations (according to users on Gartner):
- Requires use of Citrix infrastructure, which increases cost and setup complexity.
- May lag behind mainstream browsers in supporting modern web app features.
- Performance depends on the quality of Citrix configurations and network stability.

Source: Citrix
Best Practices for Enterprise Browser Management
1. Regular Security and Compliance Audits
To maintain a strong security posture, enterprise browsers should be included in routine IT security and compliance audits. These audits should verify that browser configurations align with the organization’s current security policies and compliance obligations. Key areas to assess include access control settings, data protection mechanisms, and integration with security information and event management (SIEM) systems.
Audits should also test whether policy updates are being properly enforced across all endpoints, including remote and BYOD devices. This includes evaluating the effectiveness of encryption, sandboxing, session recording, and data loss prevention (DLP) features. It’s critical to validate that the browser is capturing complete and accurate logs to support forensic investigations and compliance reporting.
Audit results should be documented with detailed findings, remediation plans, and timelines. Any discovered misconfigurations, expired certificates, or compliance deviations should trigger immediate action. Regular reviews—ideally quarterly or semi-annually—help organizations stay proactive and minimize the risk of data breaches or regulatory penalties.
2. User Training and Adoption Strategies
A successful enterprise browser deployment hinges on user understanding and cooperation. Without proper training, employees may bypass secure environments or misuse features, inadvertently introducing risk. Organizations should implement onboarding sessions that explain the browser’s role in corporate security, how it differs from consumer browsers, and what behaviors are expected.
Ongoing education should be incorporated into security awareness programs, focusing on real-world scenarios such as phishing attempts, unauthorized data sharing, and proper handling of sensitive information in SaaS tools. Interactive formats—like simulations, workshops, and knowledge checks—can improve engagement and retention.
Adoption strategies should also consider user feedback loops, offering channels for employees to report issues or suggest improvements. Providing technical support and highlighting benefits (e.g., seamless SSO, faster access to apps, or protected remote access) can help reduce resistance and increase usage. Pilot programs and role-specific configurations can further tailor the experience, ensuring minimal disruption to user workflows.
3. Extension and Plugin Management Policies
Browser extensions and plugins can expand functionality, but they also represent attack vectors if left unmanaged. A well-defined policy should govern the installation and usage of all third-party extensions. This includes maintaining an allowlist of approved tools and a blocklist for known high-risk or unnecessary add-ons.
IT administrators should leverage browser management consoles to enforce these rules at scale. This includes disabling the installation of unauthorized extensions, automatically removing unapproved tools, and preventing changes to the extension settings without admin approval. Policies should also account for updates—outdated plugins can introduce vulnerabilities even if initially approved.
Regular audits of active extensions across user devices should be conducted, along with usage analytics to identify unnecessary or underutilized tools. For high-security environments, a minimal extension policy or complete lockout may be warranted. At the same time, providing sanctioned alternatives helps balance security with usability and productivity.
4. Continuous Monitoring and Real-Time Analytics
Visibility into browser activity is vital for detecting threats, enforcing compliance, and optimizing performance. Enterprise browsers should feed telemetry data into centralized monitoring tools that track real-time behavior across users, sessions, and applications. This includes identifying high-risk actions such as large file transfers, policy violations, or the use of unsanctioned SaaS apps.
Custom dashboards should display key metrics such as session durations, blocked attempts, extension usage, and access anomalies. Real-time alerts can notify security teams of unusual patterns, like logins from unfamiliar geographies, excessive data downloads, or deviations from normal usage baselines.
Integration with SIEM and user behavior analytics (UBA) platforms improves threat detection by correlating browser activity with network, endpoint, and cloud events. Continuous monitoring not only improves security response times but also supports long-term improvements through data-driven policy refinement and risk modeling.
5. Disaster Recovery and Business Continuity Planning
Browser access has become essential for many critical business functions, especially in cloud-centric and remote-first environments. Any disruption—whether due to a cyberattack, system failure, or misconfiguration—can significantly impact productivity. A resilient enterprise browser strategy includes disaster recovery and continuity planning to address such scenarios.
This involves creating configuration backups, using centralized policy management tools to quickly redeploy settings, and maintaining failover procedures for critical access paths. Organizations should also define escalation paths and response teams for browser-specific incidents.
Testing is key. Run periodic simulations to validate recovery plans, such as restoring a user’s browser environment after device loss or revoking access in case of a compromised account. Make sure the plan accounts for different user groups, including contractors and remote workers, and that recovery timelines align with the business’s recovery time objectives (RTOs) and recovery point objectives (RPOs).
Conclusion
Enterprise browsers have emerged as critical components of modern security and IT strategies, enabling organizations to protect sensitive data, enforce compliance, and support flexible work environments. Unlike traditional browsers, they provide granular control, deep visibility, and seamless integration with enterprise infrastructure, making them well-suited for managing today’s complex threat landscape.