Which Are the Top Island Competitors?
Here is a table summarizing the key capabilities, pros and cons of the main Island Browser competitors. We go into more detail further in this article.
| Solution | Deployment Model | Browser Compatibility | Key Strengths | Common Limitations |
|---|---|---|---|---|
| Seraphic | Native browser integration | Chrome, Edge | In-browser protection; zero disruption; fast deployment | Some false positives |
| LayerX | Browser extension | Chrome, Edge | Context-aware policies; unified management; AI-aware DLP | False positives; REGEX-heavy policy config; no offline mode |
| Ericom | Remote browser isolation (RBI) | Any browser (streamed output) | Strong isolation; zero-day and phishing protection | High latency; complex deployment; costly; reduced browser usability |
| SquareX | Browser-based with remote backend | SquareX browser only | Strong GenAI and clipboard controls; built-in DLP | Short sessions; high latency; not for full-time use |
| Vivaldi | Dedicated secure browser | Vivaldi only | Deep customization; privacy-first; built-in productivity tools | High resource use; buggy sync; not optimized for enterprise security |
| Prisma | Cloud-native secure browser | Prisma browser only | Integrated with Palo Alto SASE; strong GenAI and threat protection | Poor visibility; integration issues; expensive |
| Ghost Browser | Dedicated Chromium-based browser | Ghost Browser only | Multi-session workflows; proxy and identity isolation | No mobile app; UI clunkiness; unreliable multi-login |
This is part of a series of articles about Island browser.
In this article:
- Quick Overview of Island Browser
- Limitations of Island Browser
- Notable Island Browser Competitors and Alternatives
Quick Overview of Island Browser
Island is a Chromium-based enterprise browser developed by Island Technology Inc., embedding security, governance, and productivity features directly into the browser environment.
Unlike traditional consumer browsers, Island provides organizations with granular control over user interactions, data movement, and application access. However, an important drawback of this approach is that users have to switch from common browsers like Chrome and Safari to Island, which can reduce productivity and raise compatibility issues.
Key functionalities include:
- Last-mile security controls: Administrators can enforce policies on actions such as copy-paste, downloads, uploads, and screenshots, preventing data exfiltration and ensuring compliance with organizational policies.
- Integrated identity and access management: Integration with enterprise identity providers enables single sign-on (SSO) and multi-factor authentication (MFA), ensuring secure and authenticated access to applications.
- Built-in data loss prevention (DLP): The browser incorporates DLP capabilities to detect and prevent unauthorized sharing of sensitive information.
- Context-aware policy enforcement: Policies can be tailored based on user identity, device posture, network location, and application context, allowing for dynamic and adaptive security measures.
- Visibility and analytics: Island provides detailed logging and analytics of user activity within the browser, aiding in monitoring, auditing, and optimizing user behavior and application performance.
Limitations of Island Browser
Island Browser poses several challenges, which have caused many organizations to seek alternatives. These limitations were reported by users on Gartner Peer Insights:
- Personal vs. work browser divide: Users are unlikely to replace their personal browser with Island. Maintaining two separate browser environments can be inconvenient.
- Sales experience can be frustrating: Although the technical support is strong, users have reported unexpected costs post-contract.
- UI/UX issues: Some interface bugs still exist, which can affect the overall user experience.
- Limited file interaction: While users can open internal file shares, there’s no support for editing or directly interacting with them inside the browser.
- Troubleshooting web filtering issues is complicated: When access is blocked, determining the reason isn’t straightforward. It may require using third-party tools.
- Disruptive updates: Policy or browser updates can force refreshes that interrupt user sessions and workflows.
- Resistance from users and partners: Convincing employees to switch from non-Chromium browsers or asking external collaborators to install Island can be difficult.
- VPN conflicts: Island has been known to conflict with some VPN services, leading to degraded user experience.
Notable Island Browser Competitors and Alternatives
There are several approaches to enterprise browser security. We’ll break down Island competitors by their technology approach.
Enterprise Security for Existing Browsers
Instead of replacing the user’s default browser, some solutions focus on enhancing the security of existing browsers like Chrome, Edge, or Safari. These tools run invisibly in the background or embed into the browser’s runtime environment, allowing organizations to enforce security policies without disrupting user behavior or introducing a new browser.
1. Seraphic

Seraphic Security delivers enterprise-grade browser security that works with employees’ existing browsers, eliminating the need to deploy specialized browsers that require users to change their familiar browsing environments. Seraphic provides a superior remote browser isolation technology that transforms any standard browser into a secure enterprise endpoint without disrupting user workflows or requiring browser migration.
Key features:
- Browser-agnostic security: Works seamlessly with Chrome, Edge, Firefox, Safari, and other browsers, allowing employees to maintain their preferred browsing experience while gaining enterprise protection.
- Complete remote isolation: All web content executes in secure cloud containers, ensuring zero malicious code reaches corporate endpoints, providing stronger isolation than browser-based solutions.
- Transparent deployment: Requires no browser replacement, endpoint agents, or user training, enabling rapid enterprise rollout without the adoption challenges of specialized browsers.
- Universal web compatibility: Supports all web applications, plugins, and interactive content without the compatibility limitations or feature restrictions that can affect standalone enterprise browsers.
- Enhanced user productivity: Preserves native browser performance, extensions, bookmarks, and personalization while adding enterprise security layers invisibly to the user experience.
Browser Security Extensions
Browser security extensions aim to improve existing browsers with enterprise-grade security capabilities without replacing the browser itself. These lightweight solutions run as add-ons within Chrome, Edge, or other popular browsers, allowing organizations to enforce policies, monitor activity, and mitigate risks directly at the browser level.
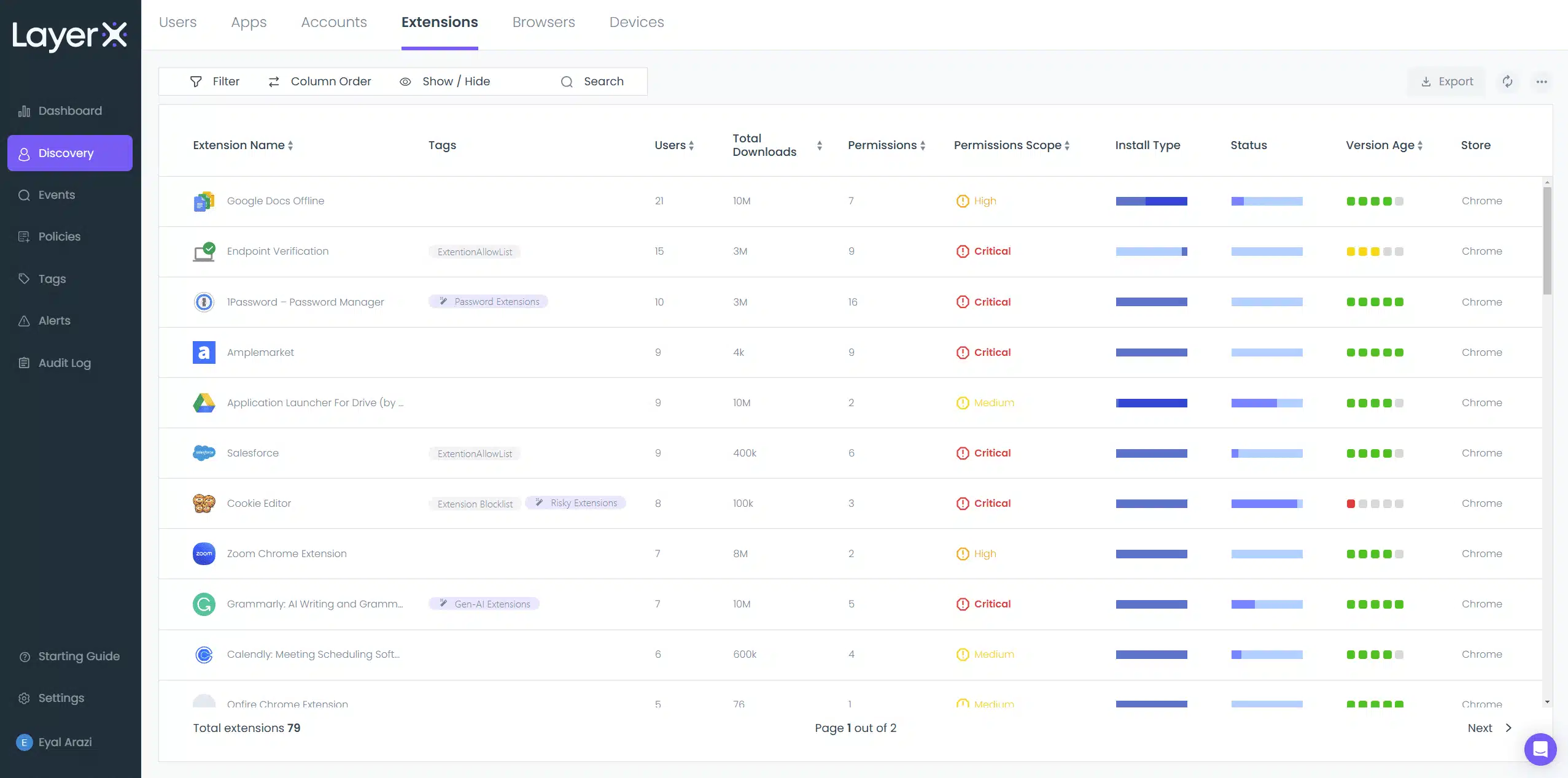
2. LayerX

LayerX is an enterprise-grade browser extension to transform standard browsers into secure, manageable work environments. Unlike full browser replacements like Island, LayerX improves existing browsers by injecting deep monitoring and security capabilities without disrupting legitimate user activity.
Key features include:
- Session analysis via Plexus Engine: Operates both locally in the browser and via a centralized cloud service. Inspects browser modifications, page behavior, and user actions.
- Adaptive risk-based policies: Policies dynamically respond to risk by restricting activity or blocking pages based on context. Administrators can set rules to act on suspicious behavior within the session.
- Malicious content detection: The extension continuously scans webpages for malicious scripts, files, or content, helping block threats before users can engage with them.
- Identity protection improvements: Can act as a secondary authentication factor, improving existing identity management tools and reducing the risk of compromised accounts.
- Unified browser management: Allows centralized configuration and monitoring across all browsers in use, regardless of type or version.
Limitations, as reported by users on Gartner Peer Insights:
- Frequent false positives: Users report numerous false positives across data loss prevention (DLP) and anti-phishing systems, which can lead to unnecessary alerts and disruptions.
- Limited platform support: The extension’s compatibility with virtual desktop infrastructure (VDI) and the Safari browser is incomplete, reducing its flexibility in certain enterprise environments.
- Lack of offline mode: Many features depend on a constant connection to the management console, limiting functionality in offline scenarios.
- Complex policy configuration: Defining policies can be challenging, often requiring advanced techniques such as regular expressions (REGEX), which increases setup time and complexity.
- Minor performance impacts: Some users have experienced slight browser slowdowns during use, though these are generally limited and resolved quickly by support.
- Restricted alerting options: The platform does not yet support automatic alert delivery through email or Slack for critical events, reducing real-time responsiveness.
Source: LayerX
Remote Browser Isolation (RBI)
Remote browser isolation (RBI) solutions reduce attack surface by running browser sessions in remote environments instead of on the user’s device. These platforms open web pages on a virtual browser hosted in the cloud or a secure container, then stream only safe rendering data to the user. However, these solutions often suffer from high latency and compatibility issues.
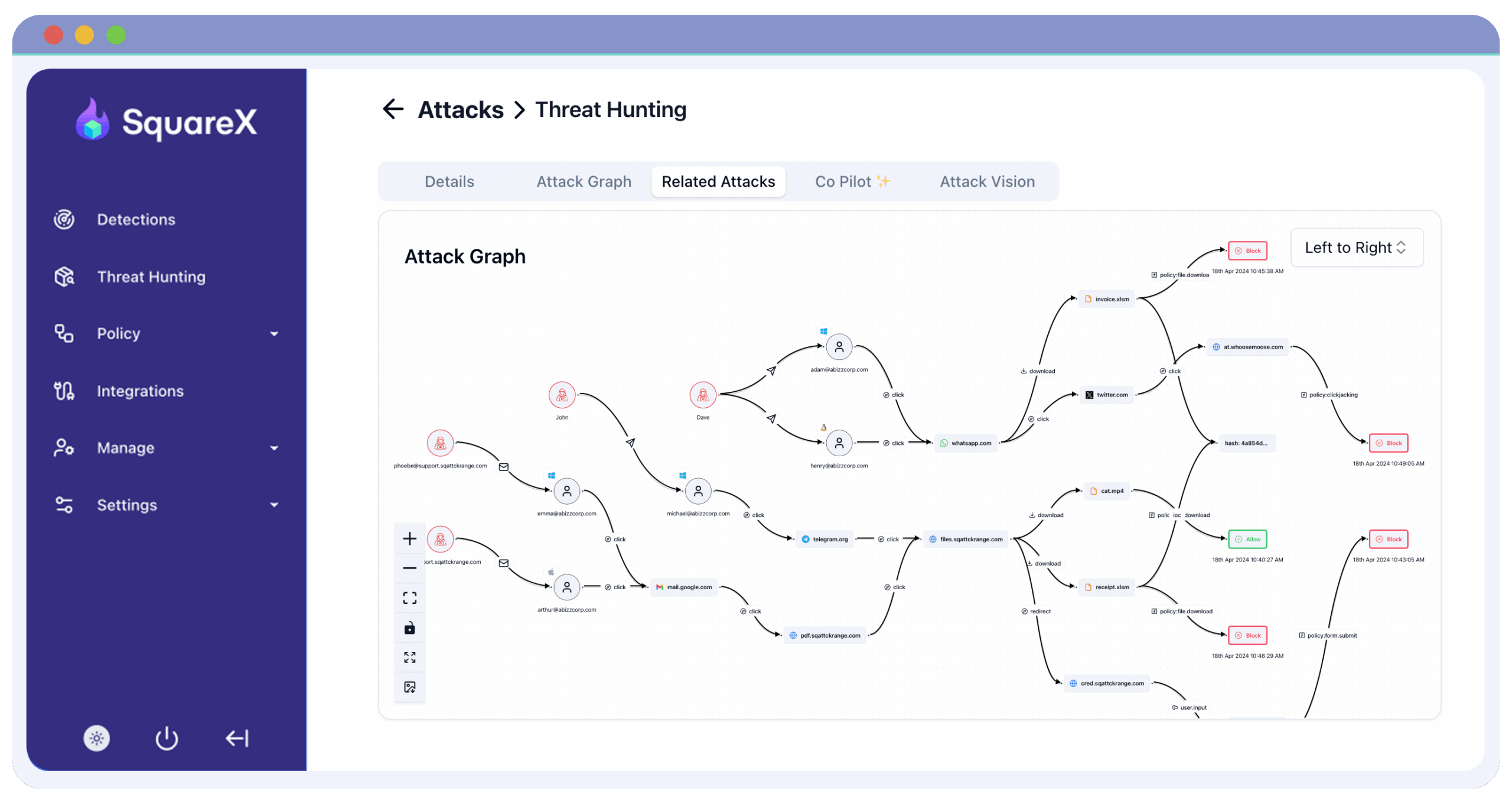
3. SquareX
SquareX is a browser-integrated data loss prevention (DLP) solution to address the security challenges posed by phishing, credential leaks, and the rise of generative AI applications. Unlike traditional SWGs and CASBs that rely on network-level traffic inspection, SquareX enforces security policies at the browser level, where most client-side interactions occur.
Key features include:
- In-browser data loss prevention (DLP): Embeds DLP controls directly into the browser, protecting against data leaks when users fall for phishing attacks.
- AI-aware security policies: Enables organizations to create controls around generative AI tools like ChatGPT. Policies can block risky actions such as pasting or uploading sensitive content into AI apps without disabling the tools altogether.
- Clipboard control for GenAI use: Admins can generate policies to block copying content into or from ChatGPT via the clipboard.
- File upload restrictions to AI apps: Employees are prevented from uploading sensitive documents to generative AI tools.
- Password reuse prevention: Can enforce unique password usage across multiple SaaS applications by generating policies that require high password strength and variation.
Limitations, as reported by PC Magazine:
- Short session duration: The browser automatically terminates sessions after 10 minutes. While this limit can be extended in 10-minute increments, it maxes out at 60 minutes, making it impractical for continuous use.
- Not suitable as a daily browser: SquareX is designed for task-specific, short-term browsing sessions. It is not intended to replace standard browsers for daily work.
- Limited disposable email feature: The platform offers very restricted functionality for disposable email use, which may be a drawback for testing or anonymous access scenarios.
- Performance overhead: All web traffic is routed through SquareX servers, which can introduce latency and slow down browsing speed.
Source: SquareX
Dedicated Secure Browsers (Like Island)
Dedicated secure browsers are standalone applications built from scratch with enterprise needs in mind. Unlike browser extensions or overlays, these solutions replace the default browser entirely, embedding controls into the core browser architecture. This allows for granular policy enforcement and integrated data protection that standard browsers can’t natively support. However, this model requires users to switch to non-standard browsers and can reduce productivity and user satisfaction.
4. Menlo
Menlo Security offers a cloud-based remote browser isolation (RBI) solution designed to eliminate malware and phishing threats by executing all web content in a remote environment. The Menlo Secure Cloud Browser renders content in the cloud and streams only safe visual data to the endpoint, ensuring isolation from potentially malicious sites.
Key features include:
- RBI architecture: Menlo renders browser sessions in a remote container in the cloud.
- Zero trust isolation for SaaS and private apps: Supports secure access to both public SaaS applications and internal apps without exposing the enterprise network.
- Phishing and malicious link protection: Prevents credential theft and malicious downloads by isolating web sessions and sanitizing file content using content disarm and reconstruction (CDR).
- Granular policy controls: Admins can set per-user or per-app policies to restrict actions like clipboard usage, file uploads/downloads, and printing based on risk context.
- User experience: Although operating in an isolated environment, the browser aims to replicate a native browsing experience with minimal lag or usability trade-offs.
Limitations, as reported by users on G2 and Gartner Peer Insights:
- Delayed response times: While generally smooth, some users noted slow performance or UI lag when accessing media-heavy or dynamic websites.
- Compatibility issues with legacy applications: Certain older internal apps or browser extensions may not function correctly within the Menlo virtual browser.
- Steep learning curve for admins: Managing and fine-tuning policies requires training and may be challenging for teams unfamiliar with RBI systems.
- Limited offline functionality: Because Menlo’s model depends on cloud-hosted isolation, users cannot access web resources when disconnected from the internet.
- Occasional login session issues: Some users have reported session timeouts or login problems that disrupted workflow, particularly during long-running activities.
Source: Menlo Security
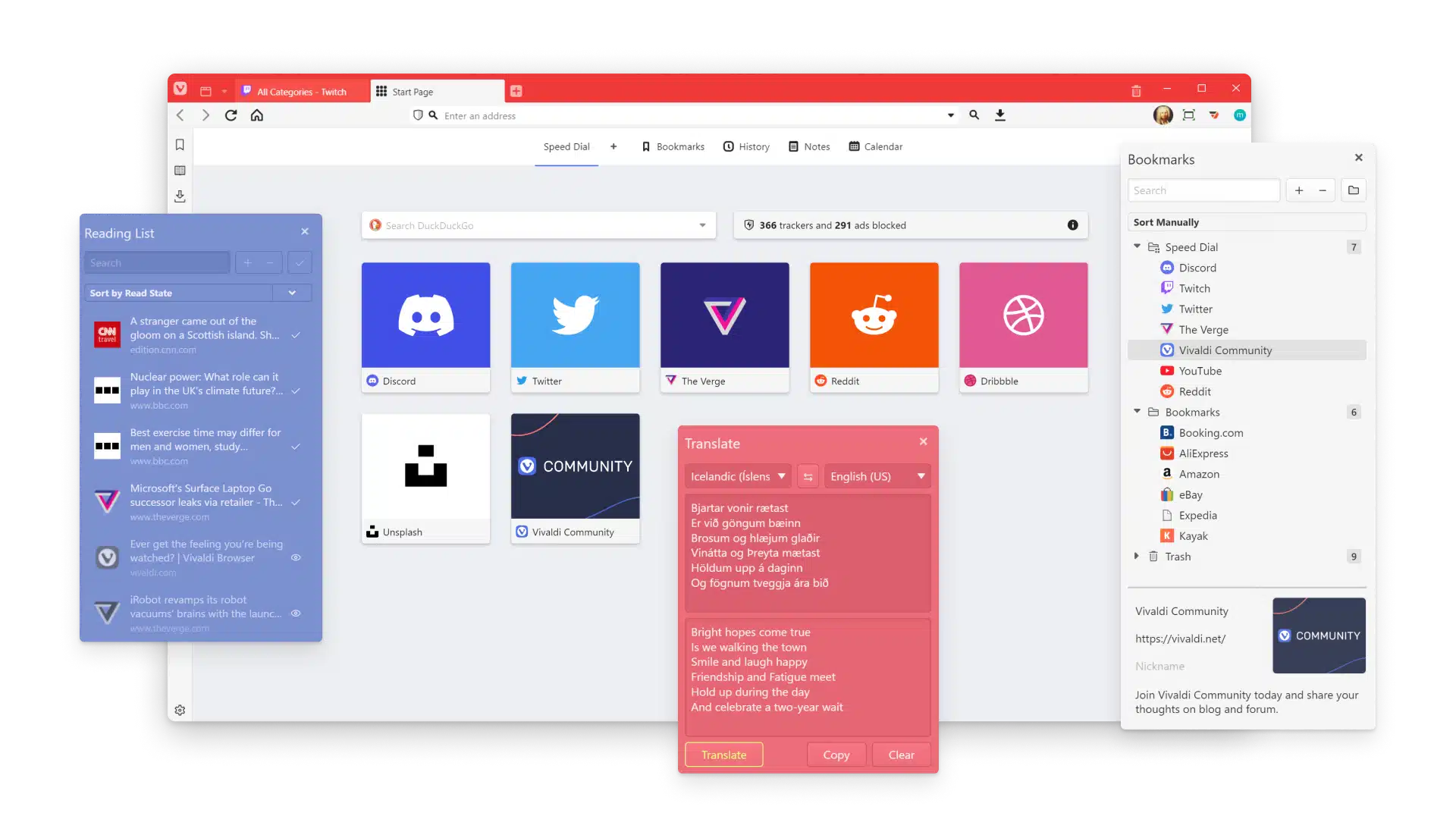
5. Vivaldi
Vivaldi is a customizable, privacy-focused web browser developed by Vivaldi Technologies. It is built for users who require control over every aspect of their browsing experience. With an anti-surveillance stance and built-in tools for productivity, organization, and personalization, Vivaldi eliminates the need for third-party extensions while maintaining speed and privacy.
Key features include:
- Built-in productivity suite: Includes a unified email client, calendar, and an algorithm-free feed reader.
- Tab management: Features like Tab Stacking, Tab Tiling, and Workspaces let users group, split, and categorize tabs for better organization and multitasking.
- Customizable interface: Users can tweak elements of the browser—from themes and keyboard shortcuts to toolbar layout and start pages.
- Privacy by design: Blocks trackers and ads by default and never profiles users. Offers end-to-end encrypted sync and integrates with Proton VPN for added privacy.
- Sidebar tools: The browser’s Web Panels allow users to dock frequently visited sites like chat apps or social feeds into the sidebar for easy access while browsing.
Limitations, as reported by users on Software Advice:
- High resource usage: Users report that Vivaldi consumes more memory and battery compared to other browsers, which can affect performance, especially on laptops.
- Occasional crashes and freezes: The browser may become unstable when interacting with certain web dialogs, such as unsaved changes alerts.
- Buggy sync across devices: Syncing data between desktop and mobile versions is not always reliable, leading to inconsistencies.
- Inefficient settings navigation: Some settings are hidden behind non-intuitive UI elements, making them hard to locate and manage.
- Slower performance: Compared to alternatives like Chrome or Brave, Vivaldi can exhibit performance drops and slower load times.
Source: Vivaldi
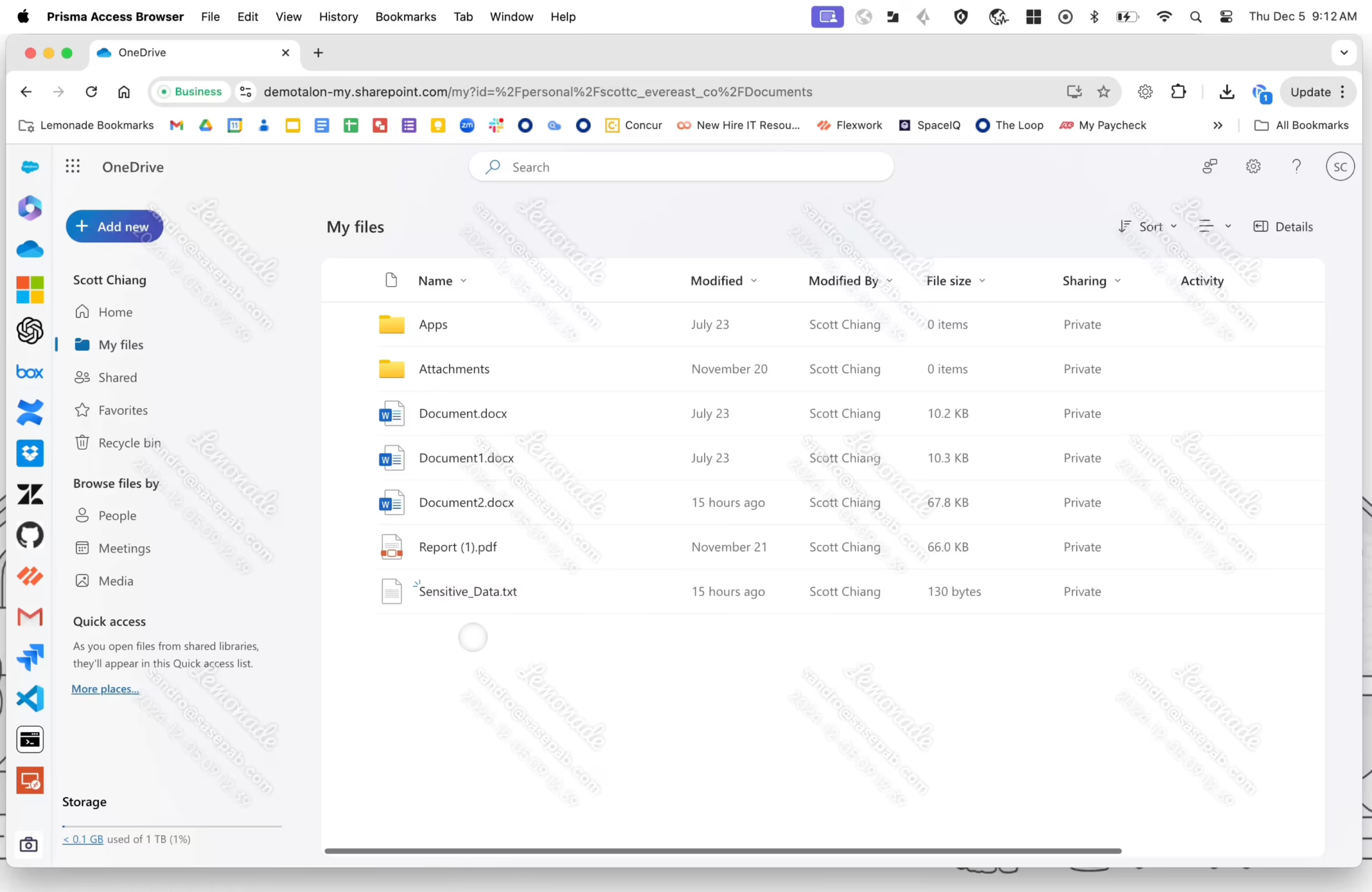
6. Prisma Access Browser
Prisma Access Browser is a secure, cloud-native browser developed by Palo Alto Networks as part of its Secure Access Service Edge (SASE) platform. Unlike traditional browsers or bolt-on security tools, it embeds security into the browser experience, delivering protections across both managed and unmanaged devices.
Key features include:
- Native SASE integration: Natively built into a full SASE stack, extends unified security policies across all users, devices, and locations.
- Zero trust access for remote and BYOD users: Applies zero trust principles to independent workers and personal devices (BYOD), enabling secure remote access without the overhead of VDI or shipping corporate laptops.
- Granular data and access controls: Administrators can enforce fine-grained security rules—such as restricting copy-paste, downloads, or app-specific behavior.
- GenAI activity monitoring and shadow AI blocking: Offers visibility into how users interact with generative AI apps, helping organizations detect risky behavior and block unauthorized AI usage.
- Threat prevention: Powered by Precision AI, analyzes billions of events daily to identify and block threats including malicious files, phishing links, and malware-laden URLs.
Limitations, as reported by users on PeerSpot:
- Limited visibility and troubleshooting: Users find it difficult to diagnose issues independently due to restricted visibility, often requiring assistance from Palo Alto support.
- Integration challenges: The browser struggles with compatibility in certain environments, particularly within healthcare systems and when integrating with third-party solutions.
- Disruptive update process: Updates can affect production environments due to poor communication and planning, making them risky in sensitive deployments.
- Uncompetitive pricing and licensing: Some users believe the cost is too high relative to the value provided, and request more flexible licensing models.
- Weak documentation and support: The quality and availability of product guides and support responses are considered insufficient for effective self-service troubleshooting.
Source: Palo Alto Networks
7. Ghost Browser

Ghost Browser is a productivity-focused browser built on Chromium, designed for professionals who manage multiple identities, sessions, and workflows across web platforms. Its primary feature is identity isolation—letting users operate different sessions in the same window, each with its own cookies, logins, and proxies.
Key features include:
- Isolated identities per tab: Users can assign permanent or temporary “Identities” to tabs, each with isolated cookie jars, allowing simultaneous logins to multiple accounts on the same site.
- Per-tab proxy control: Assigns unique proxies to individual tabs or groups of tabs. This supports tasks like geo-specific browsing, ad verification, and secure automation.
- Chrome extension compatibility: Built on Chromium and supports nearly all Chrome extensions. Users can import an extension setup in under 30 seconds.
- Sync Workspaces across teams: Shares Workspaces, Identities, cookies, and proxy settings across teams. This enables better collaboration in sales, outreach, QA, or multi-user environments.
- Time zone and hardware spoofing: With Ghost Proxy Control, users can spoof system time zones and hardware details to reduce browser fingerprinting.
Limitations, as reported by users on G2:
- No mobile app support: Ghost Browser lacks Android and iOS versions, limiting its usability for teams that rely on mobile workflows.
- High cost for limited features: Despite being a paid product, many users feel its capabilities don’t justify the price, especially when free alternatives offer similar functionality.
- Weak extension support: Although based on Chromium, its extension ecosystem is less robust than mainstream browsers like Chrome, which can hinder productivity.
- Privacy concerns: Some users express concerns over the platform’s privacy practices compared to more established secure browsers.
- Clunky user interface: The interface is considered less polished, with critiques around its cleanliness and intuitiveness.
- Unreliable multi-login functionality: The feature designed to simplify logging into multiple accounts in one window doesn’t always work as expected.
Source: Ghost Browser
Conclusion
For most organizations, the least disruptive and most scalable approach to browser security is enhancing the tools users already rely on. Solutions that secure existing browsers offer strong protection without requiring users to change their habits or adopt new software, making them well-suited for modern, hybrid work environments.