What Are Data Loss Prevention Solutions?
Data loss prevention (DLP) solutions detect and prevent unauthorized access, transfer, or leakage of sensitive information. Organizations use DLP solutions to secure data at rest, in motion, and in use, reducing the risk of accidental or malicious data breaches. These tools provide visibility into how data is handled within a network and take action when risky or non-compliant behavior is detected, such as blocking file transfers or alerting security teams to policy violations.
In an era where regulatory compliance is strict and cyber-attacks are prevalent, DLP solutions play a critical role in data security strategies. They enforce corporate policies regarding personally identifiable information (PII), intellectual property, financial information, and other confidential records. By integrating DLP into their security posture, organizations can reduce financial losses, legal penalties, and damage to brand reputation that may result from data exposure incidents.
In this article:
Key Features of DLP Solutions
Data Identification and Classification
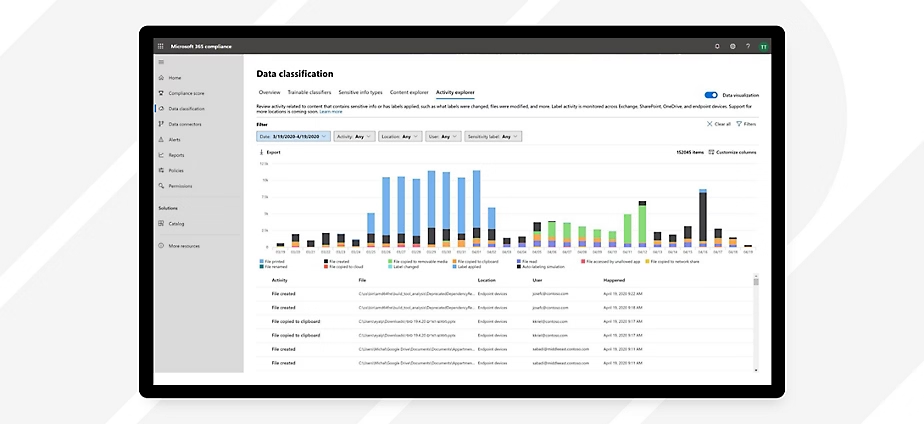
A primary function of DLP solutions is the ability to identify and classify data across the organization’s digital environment. This process involves scanning files, databases, and communications for sensitive content by using pre-defined patterns, keywords, and machine learning algorithms. Accurate identification enables DLP to differentiate between regular business data and protected information such as credit card numbers or customer databases.
Classification mechanisms then assign security labels to the located data, categorizing it by sensitivity and risk level. This structured approach allows DLP systems to apply the appropriate policies based on classification, automating the protection of high-value or regulated assets. Automated classification reduces reliance on manual user input, ensuring consistency and coverage as data flows and evolves throughout the organization.
Content Inspection
Content inspection technology enables DLP solutions to analyze actual data as it moves through endpoints, networks, or cloud environments. This examination occurs in real-time and examines file contents, document metadata, email bodies, and attachments for characteristics associated with sensitive or regulated information.
By deeply inspecting content, these systems help identify potential leaks that bypass basic perimeter defenses, such as data embedded in documents or disguised through encoding. Content inspection is critical for detecting outbound data exposures and preventing users from unintentionally sending confidential information through email, file-sharing apps, or removable storage devices.
Policy-Based Enforcement
DLP solutions rely heavily on policy-based enforcement to control how data is accessed, transmitted, or shared inside and outside an organization. Administrators define granular rules tailored to business needs and regulatory obligations. These policies specify what actions are permitted or blocked when particular types of data are detected, such as encrypting a message containing PII, requiring user justification, or outright blocking transfers.
Policy-driven controls are flexible and adaptable, supporting a variety of enforcement actions based on user role, source, destination, and context. This enables organizations to balance security with productivity—blocking risk when necessary without halting legitimate business operations.
Learn more in our detailed guide to data loss prevention policy
Encryption and Access Controls
Encryption and access controls work in tandem with DLP solutions to protect sensitive data. Encryption secures data by encoding it at rest or in transit, making it unreadable without proper authorization. DLP policies can trigger automatic encryption for emails, files, or storage containing confidential information, adding a critical layer of security, particularly when data leaves controlled environments.
Access controls work by restricting who can view, modify, or share specific data based on identity, role, or device compliance. Integrated DLP platforms enforce these restrictions dynamically, preventing unauthorized access to protected files even when the data travels beyond corporate boundaries.
Regulatory Compliance Support
Many organizations deploy DLP solutions to help meet specific regulatory compliance mandates, such as GDPR, HIPAA, or PCI-DSS. DLP systems provide templates and predefined policies tailored to these requirements, ensuring that sensitive categories of data are automatically recognized and protected according to the relevant standards. They generate audit logs and reports that demonstrate compliance during external assessments or investigations.
Beyond detection and prevention, compliance support features simplify policy management and streamline risk assessment processes. DLP solutions help security teams quickly identify at-risk data or policy violations, facilitating remediation before a breach occurs or regulators intervene.
Categories of DLP Solutions
Browser-Based DLP
Browser-based DLP focuses on monitoring and controlling sensitive data as users interact with web-based applications and resources. With the shift towards hybrid work and the growing use of SaaS platforms, browsers have become a common channel for both intentional and accidental data leaks. Employees and contractors can easily download corporate data from web apps and upload it to personal cloud storage, exposing organizations to data loss risks.
Browser-based DLP solutions address these challenges by applying controls directly within the browser environment. They can enforce restrictions on user actions such as copy-paste, printing, screen capture, or file uploads and downloads. These solutions also provide content inspection capabilities to detect sensitive information in web traffic and downloaded files.
Network DLP
Network DLP operates at the network perimeter and monitors all inbound and outbound traffic for sensitive information. These solutions analyze emails, web traffic, file transfers, and other data streams, searching for patterns that match policy-defined data types such as PII, intellectual property, or financial records. Network DLP acts as a gatekeeper, enabling organizations to block, quarantine, or encrypt sensitive data before it leaves the company network.
By monitoring data flows in real-time, network DLP provides broad coverage across the entire organization, regardless of endpoint device or user role. This central point of control is particularly effective for catching data leaks resulting from social engineering attacks, misdirected emails, or unauthorized uploads to cloud services. It is commonly deployed as hardware appliances, virtual appliances, or cloud services.
Endpoint DLP
Endpoint DLP extends protection to individual devices such as desktops, laptops, and workstations. It enforces security policies directly at the device level, monitoring user actions like file copying, printing, screen capturing, and transferring data to USB drives or external devices. Endpoint DLP is vital for organizations that support remote work or manage large fleets of unmanaged endpoints.
By operating on endpoints, these solutions address insider threats and data leaks that occur outside traditional network boundaries. Endpoint DLP can prevent unintentional exposures caused by human error, as well as stop malicious attempts by users seeking to exfiltrate sensitive data. Integration with remote management tools allows policies and protections to persist even when users are offline or working from home.
Cloud DLP
Cloud DLP addresses risks associated with storing and processing sensitive information on cloud platforms. These solutions integrate with software as a service (SaaS) applications, cloud storage, and infrastructure as a service (IaaS) providers to monitor and control data as it moves to, from, and within the cloud environment. Cloud DLP uses APIs and built-in connectors to inspect documents, emails, and communication channels for policy violations or misconfigurations.
With increasing cloud adoption, cloud DLP is essential for ensuring continuous data visibility and enforcement. These solutions support collaboration without compromising security, allowing organizations to extend DLP coverage across hybrid environments. Cloud DLP also provides automated compliance checks and integrates with other cloud security tools, helping maintain a unified security posture across multiple platforms.
Email DLP
Email DLP specializes in monitoring, identifying, and controlling sensitive data sent via corporate email systems. It scans the contents and attachments of outgoing emails, detecting patterns indicative of confidential or regulated information such as credit card data or trade secrets. Email DLP then enforces policies to block, quarantine, or encrypt messages that breach defined security thresholds.
Given that email remains a primary threat vector for data leaks, phishing, and business email compromise, email DLP is crucial for any security strategy. These solutions help organizations reduce the risk of compliance violations and data breaches by preventing careless or intentional disclosures through corporate communication channels. Integration with common email gateways and cloud-based mail services streamlines deployment and policy enforcement.
Notable DLP Solutions
1. Seraphic Security
DLP category: Browser-based
Seraphic Security enhances Data Loss Prevention (DLP) strategies by securing the browsers, which is the primary interface for SaaS, internal apps, and file sharing. Seraphic does this without relying on intrusive agents or complex network routing. Unlike traditional DLP solutions that operate at the network or endpoint level, Seraphic applies data protection policies directly in the browser, where data is accessed, manipulated, and potentially exfiltrated. This allows organizations to enforce precise controls and stop data leakage at the source, without impacting user experience.
Key features include:
- Granular data control in the browser: Enforces policies on uploads, downloads, copy-paste, screen capture, printing, and form submissions across web applications and cloud services.
- Context-aware policy enforcement: Applies DLP rules dynamically based on user identity, device posture, browser type, content sensitivity, and risk level.
- No agents, no traffic redirection: Deploys quickly without installing endpoint agents or rerouting traffic through proxies, ensuring coverage on both managed and unmanaged devices.
- SaaS and shadow IT governance: Detects and controls usage of unsanctioned SaaS applications and personal accounts, preventing unauthorized data transfers.
- Integrated browser telemetry: Captures detailed logs of browser interactions and policy enforcement actions for audit, compliance, and incident response.
Source: Seraphic Security
2. Microsoft Purview DLP
DLP category: Cloud and endpoint
Microsoft Purview Data Loss Prevention is a cloud-native solution that helps organizations protect data across their digital environment, including endpoints, Microsoft 365 apps, and Microsoft 365 Copilot. It prevents unauthorized sharing, transfer, or use of confidential information through adaptive controls.
Key features include:
- Comprehensive protection: Detects and protects sensitive data across devices, services, and apps, including Microsoft 365 Copilot.
- Cloud-managed deployment: Manages the entire DLP lifecycle through a single cloud-native platform.
- Adaptive controls: Uses machine learning to analyze behavior, classify data, and apply policies dynamically.
- Single policy management portal: Lets users create, modify, and enforce DLP rules from a centralized compliance portal.
- Integration with Microsoft Purview information protection: Combine DLP with Microsoft’s information protection tools for consistent labeling, classification, and control of sensitive content.
Source: Microsoft
3. Google Cloud DLP
DLP category: Cloud DLP
Google Cloud Data Loss Prevention, now part of the Sensitive Data Protection suite, helps organizations discover, classify, and secure sensitive information across cloud and hybrid environments. Designed for both structured and unstructured data, it enables scalable inspection and transformation of data.
Key features include:
- Automated discovery and classification: Profiles sensitive data across BigQuery tables and projects using predefined detectors.
- De-identification and data obfuscation: Applies masking, tokenization, bucketing, and other techniques to reduce data exposure.
- Integrated security intelligence: Users can feed data insights into Chronicle and Security Command Center to prioritize threats and simplify security investigations.
- Dynamic and fine-grained masking: Enables column-level controls and dynamic masking policies based on classification outcomes.
- AI/ML data minimization: Protects privacy in AI applications by classifying and de-identifying sensitive elements in training data, feedback, prompts, and responses.
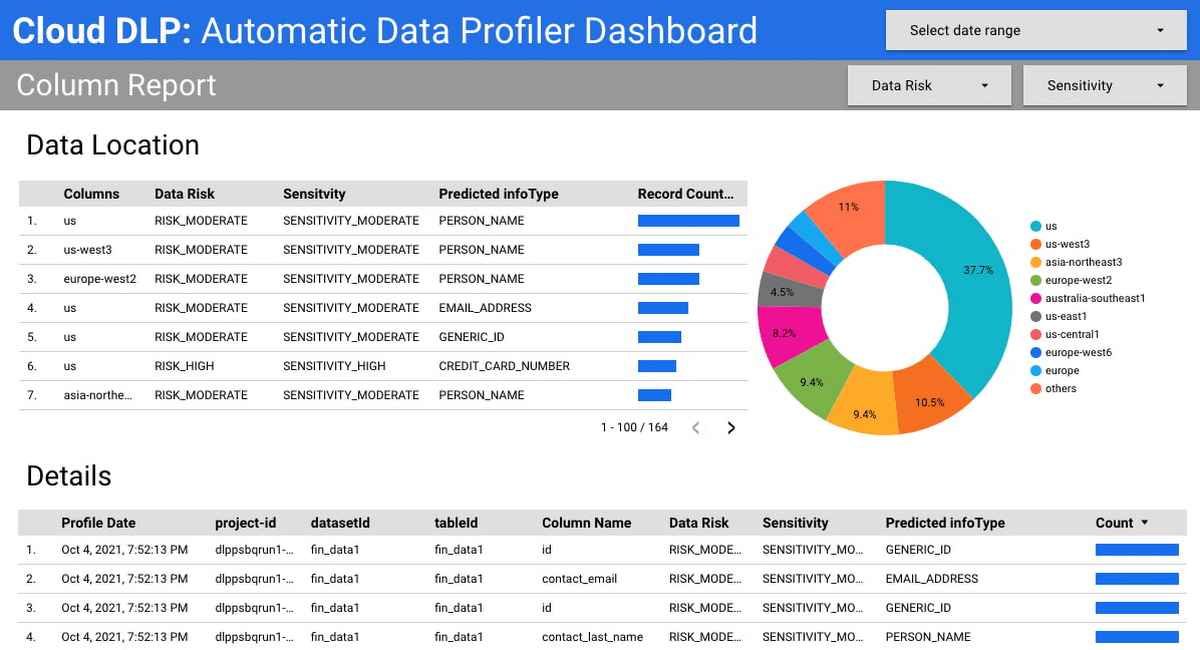
Source: Google Cloud
4. Forcepoint Data Loss Prevention
DLP category: Cloud and endpoint
Forcepoint Data Loss Prevention is a risk-adaptive solution to protect data across cloud, on-premises, and hybrid environments. With a unified platform for managing policies, monitoring activity, and responding to incidents it helps organizations prevent data leaks, simplify regulatory compliance, and adapt to user risk.
Key features include:
- Unified policy management: Centrally configures, manages, and enforces DLP policies across endpoints, cloud apps, email, and web.
- Risk-adaptive protection: Automatically adjusts enforcement actions based on user behavior analysis using user and entity behavior analytics (UEBA).
- Fingerprinting & classification: Helps identify and classify data with fingerprinting and an AI-driven mesh classification engine.
- Cloud and on-premises deployment: Deploys as a SaaS solution or on-premises.
- Compliance support: Offers over 1700 classifiers and pre-built policy templates to meet mandates like GDPR and HIPAA.
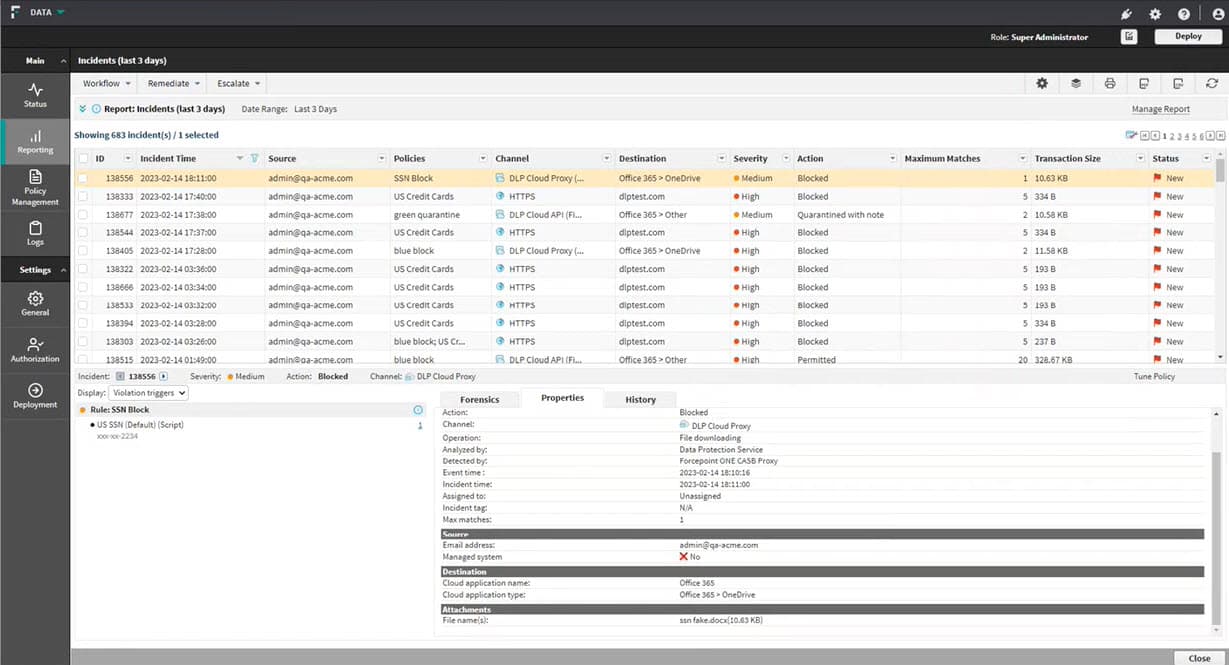
Source: Forcepoint
5. Broadcom DLP
DLP category: Network and endpoint
Symantec Data Loss Prevention by Broadcom is a solution intended to deliver accurate, scalable, and adaptive protection for data across endpoints, networks, cloud services, and storage. It combines content-aware detection with policy enforcement to help organizations reduce data breach risks and ensure compliance with global regulations.
Key features include:
- Data discovery: Scans endpoints, databases, file shares, and cloud platforms to locate sensitive data across the enterprise, using detection techniques like exact data matching (EDM), indexed document matching (IDM), and sensitive image recognition via OCR.
- Content-aware monitoring: Helps understand how data is used and shared across endpoints, email, web traffic, and cloud apps.
- Unified policy framework: Applies a consistent set of DLP policies across cloud and on-premises environments through a web-based console.
- Data leakage prevention: Prevents data exfiltration through blocking, quarantining, or notifying users when policy violations occur.
- Incident remediation & automation: Offers workflows and integrations with tools like ServiceNow to decentralize and simplify incident response.
Source: Broadcom
6. Trellix Data Loss Prevention
DLP category: Network and endpoint
Trellix Data Loss Prevention is a modular, policy-based solution to protect sensitive data across endpoints, networks, email, and storage systems. It offers visibility and control over data throughout its lifecycle, enabling organizations to identify critical assets, classify them, and apply contextual protections.
Key features include:
- Data classification: Helps discover and classify sensitive or proprietary data across multiple environments using exact data matching and auto-classification.
- Lifecycle-based protection: Monitors and enforces policies across data at rest, in motion, and in use, with protection extending to endpoints, web traffic, email systems, file shares, and cloud repositories.
- Endpoint protection: Trellix DLP Endpoint Complete secures data on Windows and macOS devices with features like content filtering, user coaching, and data blocking.
- Network-level controls: Trellix DLP Network Prevent and Network Monitor inspect data traversing networks, email, and web channels.
- Data discovery & inventory: Trellix DLP Discover enables organizations to scan and classify data across file repositories and networks, enforce rights management, and manage data handling.
Source: Trellix
7. Proofpoint DLP

DLP category: Cloud and endpoint
Proofpoint Data Loss Prevention modernizes legacy DLP approaches with a human-centric, cloud-native platform that protects data across email, cloud services, and endpoints. Focused on understanding user behavior and intent, it combines content inspection with analytics to detect and prevent careless, compromised, and malicious data activity.
Key features include:
- Cross-channel visibility: Monitors data interactions across email, cloud apps, and endpoint devices to detect and investigate threats.
- User behavior analysis: Instead of relying on static rules, factors in user intent and risk level.
- Integrated incident management: Centralizes alert triage and simplifies response workflows.
- Cloud-native architecture: Deploys rapidly with lightweight agents, auto-scales as needed, and helps maintain system performance with minimal overhead.
- Privacy by design: Protects user identities with anonymization, role-based access, and support for global data residency requirements.
Source: Proofpoint
8. Netskope DLP
DLP category: Cloud and endpoint
Netskope Data Loss Prevention is a cloud-native solution that offers visibility, control, and protection for sensitive data across cloud, web, email, endpoints, and networks. It enables policy enforcement from a centralized platform, helping organizations prevent breaches, comply with regulations, and securely enable emerging technologies like generative AI.
Key features include:
- Data visibility: Automatically discovers and classifies sensitive data, including PII, financial records, and intellectual property, across environments.
- Context-aware data protection: Helps understand data usage in context to apply more accurate and effective policies.
- Unified policy enforcement: Centrally manages DLP policies across endpoints, SaaS applications, cloud services, email, and user activities.
- Generative AI protection: Enables secure use of tools like ChatGPT by monitoring and controlling data interactions, helping mitigate risks of AI-driven content generation.
- Response & remediation: Detects policy violations and applies immediate responses such as blocking, alerting, or encrypting data, with options for user coaching to guide secure behavior.
Source: Netskope
Conclusion
DLP solutions are essential components of a modern cybersecurity strategy, providing organizations with the visibility and control needed to protect sensitive information across diverse environments. By combining content inspection, data classification, and policy-based enforcement, DLP systems help prevent data leaks whether they occur through email, cloud services, web apps, or endpoint devices.